In the nuclear energy sector, cybersecurity is inextricably linked to day-to-day operations. It directly impacts physical safety, system reliability, and regulatory compliance, which makes it a persistent challenge to protect highly sensitive systems without interrupting the work required to keep them running safely.
A central pillar of nuclear cybersecurity is the use of air-gapped and segmented networks. Isolation remains one of the essential risk-reduction practices across the industry. Yet even the most isolated environments depend on data moving in and out. Software updates, diagnostics, engineering files, and maintenance data must cross security boundaries, often under strict procedural controls.
These transfers often rely on removable media and transient devices. USB drives, portable storage, maintenance laptops, and contractor equipment are still widely used to bridge gaps between secure and less-trusted domains. While operationally necessary, these pathways can introduce cyber risk if not governed consistently and securely.
This operational reality was well understood at UK-based Urenco, a global provider of uranium enrichment services. The company’s facilities are deliberately divided into high-risk zones to protect people, assets, and the environment. However, files and system data must routinely traverse these different tiers to support maintenance, engineering, and operational activities.
“In our estate, removable media and transient devices are unavoidable conduits between secure and less-trusted domains in order to perform updates and diagnostics,” said Dan Mosca, head of OT cybersecurity and cyber assurance at Urenco.
Over time, Urenco implemented multiple layers of manual checks and traditional procedures to manage these transfers. While effective in preventing incidents, those controls varied from site to site and therefore depended heavily on people and paperwork.
Beyond compliance, it was important to ensure that routine operational tasks did not gradually weaken the protections that air gaps were meant to provide.
“Urenco required greater Control, Security, and Visibility into files as they cross all Urenco’s boundaries,” Mosca said. “We needed to modernize and simplify our procedures and orchestrate many of the processes that are currently in place.”
This realization marked a turning point in how file movement and removable media were managed across Urenco’s global operations.
When Routine Controls Stop Scaling
For years, Urenco managed file transfers and removable media risks through a combination of established procedures, manual checks, and site-specific cybersecurity measures. Redundancy was viewed as a strength, and every task was handled with caution. At the individual site level, this approach worked: risks were identified in time, and incidents were avoided.
The strain emerged when the same practices were repeated across the entire global organization. Each facility had developed its own variations in how files were scanned, approved, transported, and then released into secure environments. Differences were often subtle, shaped by local layouts, staffing models, and historical tooling. Over time, cybersecurity began to feel fragmented, especially for teams supporting work across multiple locations.
In addition, manual processes carried an operational cost. Staff were required to physically walk removable media across large sites, repeat scans at multiple checkpoints, and document each step for audit purposes. These tasks took time away from primary operational and engineering responsibilities and introduced fatigue into manual processes.
Supply chain interactions added further complexity. Vendor laptops and contractor systems were essential for maintenance and diagnostics, yet they arrived with varying configurations and security postures. Each connection required careful validation, which further increased the workload on both security and operations teams.
Urenco’s concern was not that these controls were ineffective, but that they were becoming harder to sustain consistently. As digital activity and regulatory expectations rose, the organization reached a common challenge for nuclear operators: manually intensive controls do not scale easily.
What Urenco needed was not more checks but more consistency. The goal became finding a way to apply the same level of scrutiny to every file and device, at every site, without slowing down the work required to keep facilities operating safely and efficiently.
Moving From Fragmented Controls to a Standardized Approach
Once Urenco stepped back and viewed file movement and removable media as a shared operational challenge, the path forward became clear. The goal was not to eliminate data transfers, which would have been impractical, but to introduce a more consistent and controlled way to handle them across all sites.
Urenco defined a set of requirements that focused on outcomes rather than individual tools. Any new approach had to apply the same level of scrutiny to every file, regardless of how or where it entered the environment. It also had to reduce reliance on manual decision-making, limit variation between facilities, and provide clear visibility for both operators and auditors. Just as important, it needed to fit into existing workflows without becoming a bottleneck.
To meet those objectives, the company implemented an integrated file and device inspection approach using OPSWAT’s MetaDefender platform. Removable media and transient devices were routed through defined checkpoints, where files could be scanned, verified, and released consistently. This shifted critical security decisions away from ad hoc, site-specific processes and into a common framework that could be applied globally.
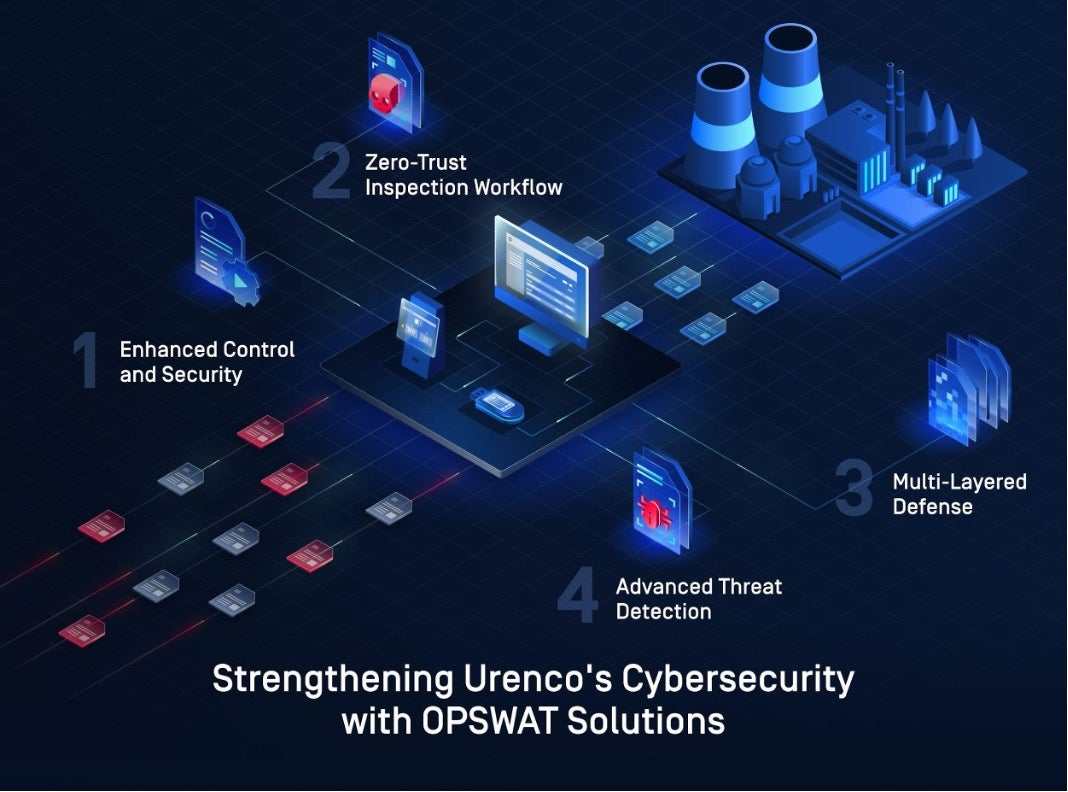
By deploying the integrated OPSWAT platform across all global facilities, Urenco ensured every file entering the nuclear environment is subject to zero-trust inspection workflows.
The approach emphasized layered inspection, where files were treated as untrusted by default and subjected to multiple checks before entering protected environments. At the same time, the process was designed to respect operational speed. Scanning and validation were integrated into daily routines rather than added as separate, time-consuming steps.
Technology played a role in enabling this shift, with Urenco deploying an integrated platform to support standardized inspection, device validation, and centralized oversight. The emphasis, however, was less on the technology itself and more on what it enabled: consistent execution, reduced variation, and greater confidence that routine actions were not undermining the protections provided by air-gapped systems. With a common model in place, Urenco was able to move from managing risk one transfer at a time to managing it systematically across its global operations.
Operational Results That Matter on the Plant Floor
Standardizing how files and devices were handled impacted more than just security posture. It altered the daily experience of the people responsible for keeping Urenco’s facilities running. Tasks that had once required multiple manual steps and repeated checks became more predictable, reducing friction in routine maintenance and engineering work.
One of the most immediate benefits was time. Staff no longer had to wait for lengthy, inconsistent scanning processes or physically transport media between multiple checkpoints.
“Everyone’s job is hard enough as it is without spending half an hour waiting for your USB drive to scan,” Mosca said.
Consistency also reduced the likelihood of manual mistakes. By applying the same inspection and validation process across sites, Urenco lowered the risk that a file would be handled differently simply because it entered through a different facility or team. This was particularly valuable when working with contractors and vendors, whose systems could be validated before they were granted access to secure environments.
The approach improved visibility and audit confidence as well. Centralized oversight made it easier to demonstrate that controls were being applied uniformly, supporting regulatory reviews without adding new administrative burden.
For operations teams, investing a small amount of time upfront to verify files and devices reduced the risk of far more disruptive events later, a tradeoff Mosca noted was minimal compared with the potential recovery time from a major outage.
Turning Routine Controls into Operational Strength
For nuclear operators, cybersecurity challenges usually emerge quietly through routine tasks such as moving files, connecting devices, and supporting maintenance work. Urenco’s experience shows that these everyday interactions deserve the same level of attention as more visible safety systems. As Mosca noted, the goal is not to slow operations in the name of security, but to ensure that security supports safe, reliable performance over the long term.
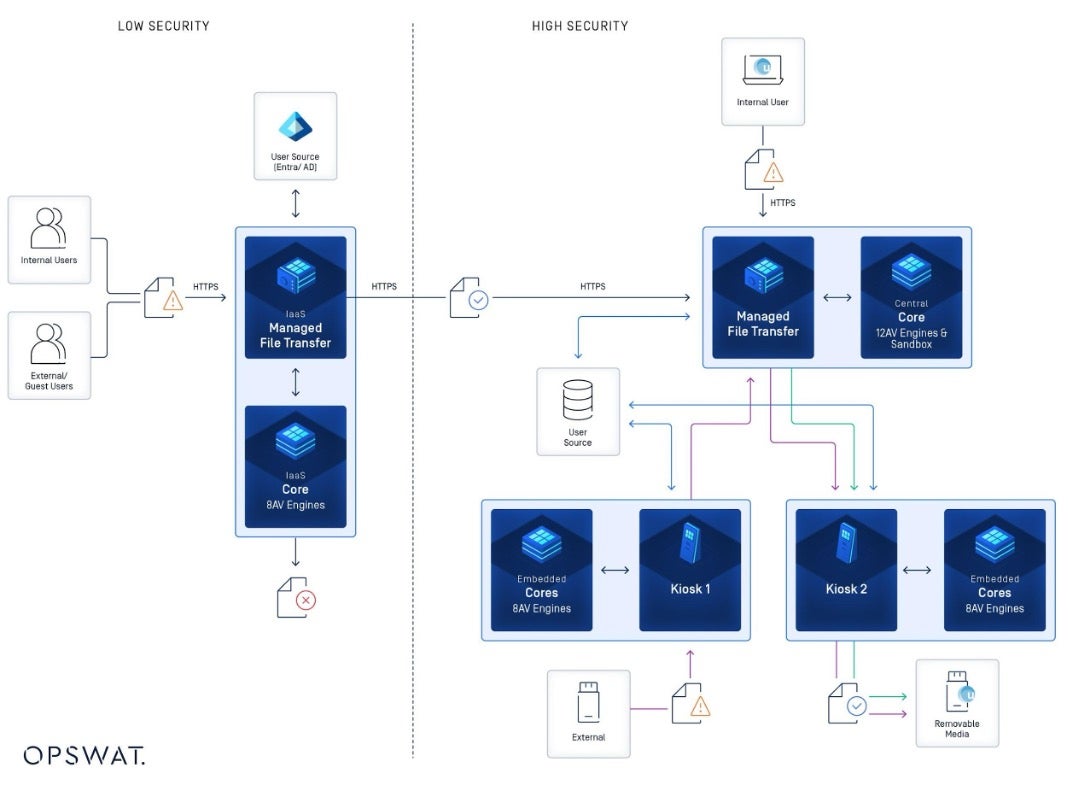
Urenco is expanding its investment in OPSWAT by adopting MetaDefender Managed File Transfer. The platform adds layered controls such as supervisor approval and release management to prevent outbreaks while enabling secure global file exchange for internal teams and external partners.
By standardizing how files and devices cross security boundaries, Urenco was able to reduce operational delays while strengthening confidence in its cybersecurity measures. Controls that rely heavily on manual effort and local variation become harder to sustain as digital activity grows. Consistency, visibility, and workflow integration matter as much as the technologies behind them.
—Simon Giddings is a seasoned professional in the technology and cybersecurity sectors, currently serving as Regional Sales Manager at OPSWAT since September 2023.