How to Manage Cyber Risk as Grid Modernization Efforts Intensify
A survey of chief information security officers revealed great insight on cyber risks and perceived vulnerabilities. While some insiders may think working hand-in-hand with government agencies to develop sound cyber protection plans will only create additional regulations to comply with, the truth is, collaboration may be the only way to ensure all threat vectors are addressed.
Few sectors face as much disruptive change in the years ahead as power and utilities (P&U), with the mantra of decarbonization, decentralization, and digitization continuing to grow more intense. Amid this rapid evolution, P&U companies have new opportunities to thrive—and so do cyber criminals eager to exploit new vulnerabilities, which in turn has triggered greater scrutiny from the Biden administration.
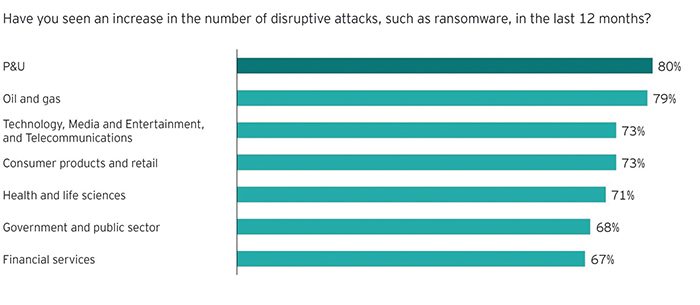
Within the P&U sector, 53% of chief information security officers have never been as concerned as they are now about their ability to manage the threat, according to the EY Global Information Security Survey 2021. About 80% have seen an increase in disruptive attacks in the past 12 months (Figure 1)—the highest rate among all sectors—and 43% believe it is only a matter of time before their organization suffers a major breach that could have been avoided if they had received additional investment. With 37% reporting that attackers are primarily targeting their industrial control systems—substantially more than any other attack vector—it’s no wonder that the White House asked P&U leaders to be part of a cyber summit on securing the nation’s critical infrastructure, and that the Transportation Security Administration has been working on enforceable new guidelines for pipelines, for example.
 |
|
1. This graphic created based on responses to the EY Global Information Security Survey 2021 shows the percentage of respondents from various industry sectors—including power and utilities, oil and gas, and technology, media, and telecom (TMT)—when asked if they had seen an increase in the number of disruptive attacks, such as ransomware, in the last 12 months. Courtesy: Ernst & Young Global Limited |
The risks are evident in how the sector is evolving. Technology and innovation are enabling the energy transition: today, different hardware components are networked with each other, often on decades-old infrastructure, and controlled by intelligent software. Every sensor and smart meter contributes to a more interconnected data-dependent energy world—and it must be protected. These trends have become supercharged amid new momentum for decarbonization, and in how P&U companies have responded to the challenges of the COVID-19 pandemic. As P&U companies put more money and effort into grid modernization, they must be vigilant and proactive against a shifting environment of cyber threats—as a smart business strategy and also increasingly as a regulatory imperative.
Evolving Vulnerabilities
In the EY survey, 81% of cyber leaders across all sectors said that the rapid response to COVID-19 forced organizations to bypass cybersecurity processes. “Shadow IT” has emerged, in which the business is making technology decisions and potentially opening backdoors, sometimes sharing data or creating connections without understanding the security implications. Meanwhile, more employees and third parties are remotely accessing systems, devices, and data, sometimes under the guise of real-time maintenance. Challenges include controlling the supply chain and fully understanding risks that devices and their components introduce to the install base. In the same survey, 40% of P&U cyber leaders warn that hackers are consistently experimenting with new strategies, such as targeting weak links in the supply chain that may override the security systems in place.
Similarly, electric grids are increasingly becoming more connected to distributed energy resources (DERs) and third parties, as part of the acceleration toward decentralization. Today, home solar power systems continue to grow more affordable, positioning more customers—or, rather, “prosumers”—to put excess energy capacity into the grid. Many more of these DERs, of which solar photovoltaics is just one part, add new complexity and connection points in electricity distribution that hackers can target. Decentralization and digitization will only increase as the Biden administration has set a target for a carbon-pollution-free power sector by 2035 and net-zero-emissions economy by 2050.
The Biden administration is also working to patch up another prominent vulnerability in the sector: ransomware attacks. From the EY survey, 40% of P&U leaders believe that state-affiliated actors are behind the breaches they have suffered (compared with 24% across other sectors). The administration issued an executive order in April to enhance the cybersecurity of electric utilities’ industrial control systems and secure the energy supply chain, and the Department of Energy is seeking more than $200 million in its fiscal 2022 budget request to address digital vulnerabilities in the sector.
Leading Practices
Beyond basic hygiene, P&U companies must adopt a security-by-design mindset: the business must set and understand cybersecurity principles and objectives so they’re considered when new products and services are introduced and technology is deployed, not grafted on after the fact. P&U leaders reported that only 37% are being engaged with adequate time by the business to address cybersecurity for new technology being implemented. Considering the risk environment, cybersecurity should always be consulted early in the design or pre-implementation phases of a project—whether it’s for a rollout of smart meters and other intelligent grid digital assets, or within traditional power plants or renewable installations, for example.
Aligning to a zero-trust architecture (ZTA) equips organizations to achieve this by default, because the key principles mandate that your assets connect to other resources only with a business reason and authorization. Amid a proliferation of connected devices and cloud technology, ZTA is oriented around what devices and components do, more than where they come from, and “zero trust” means that verification is required for each connection. This replaces outdated strategies focused on securing a perimeter around a network and scrutinizing those outside that perimeter, as a trusted device in the wrong hands can still inflict serious damage, and the bounds of the perimeter can be hard to define. In May, the Biden administration issued an executive order on cybersecurity explicitly stating that the federal government is moving toward adopting ZTA, and the Department of Energy is likely to endorse ZTA in its sector-specific cybersecurity initiative, still under development.
While technology developments have opened up new potential for attacks, they also offer new methods for bolstering defenses. Monitoring and recognizing malignant activity with this environment of connected devices and cloud access goes beyond what is humanly possible to track. Therefore, security teams need visibility at an automated scale—relying on artificial intelligence, for example, to identify and surface anomalies, prioritized by risk.
Sophisticated P&U companies are also building or leasing lab time to test their hardware, software, and communication protocols and networks before committing to large deployments—an ahead-of-the-curve approach for embedding security by design. This exercise could include mocking up the current grid, bringing potential new devices into the existing environment, and testing for unexpected vulnerabilities and potential issues related to performance.
Leading individual P&U companies, device manufacturers, consultancies, and some industry groups have also created OT “honeypots.” The basic idea is to create a mockup of a device or set of devices, let them be “visible” to the internet, and then collect and analyze data related to how and how quickly the device is identified and what threats surface. The organizations can then use that information to determine where and how to evolve defenses.
Getting More Internal and External Help
Cybersecurity leaders wishing to pursue such strategies may find themselves crashing against internal roadblocks: without strong ties to the business, their functions are easily cast as an inhibitor rather than an enabler. Just 46% of P&U respondents in the EY survey are confident in the security team’s ability to speak the same language as peers in the business, and only 31% believe they are seen as supporters of innovation (Figure 2).
 |
|
2. This graphic shows the percentage of responses received from personnel in the human resources (HR), business line, and product development/research and development (R&D) departments of companies that participated in the EY Global Information Security Survey 2021 when asked to describe the relationship between the security team and other functions of their companies. Courtesy: Ernst & Young Global Limited |
Compared to other sectors, P&U faces a unique challenge in that investments are driven by an expectation of a rate of return over time, and cybersecurity is labeled an operating expense. Amid tight budgets, boards are prioritizing functions where there is a clear route from investment to added value. Therefore, they can be more receptive toward buying tools to save money—but not optimizing or maintaining them. Security leaders should make the case that investing wisely and getting the most out of their tools enables the business to make smarter decisions on risk. Most of us don’t think twice about getting on a plane and flying through the air at 500 miles per hour at 36,000 feet, because the security protocols in place make us feel protected. Similarly, the business can accelerate its plans and reach new heights if its cybersecurity protections instill the right level of confidence.
It’s also worthwhile to look outside your organization, including at public-private partnerships and collaboration opportunities. Executives may fear that when they have conversations with regulators, or other parts of the government that may interact with regulators, that they’re going to legislate what must be done. This risks adding to what is perceived as an already significant compliance burden. However, because these risks are to our nation’s critical infrastructure, and not just to one company’s equipment, P&U organizations cannot always effectively mitigate risks independently. The way for these discussions to be most impactful and focused is strong engagement between industry and regulators.
While the battle against digital threats continues to grow more intense and complex, P&U companies are making progress. Increasingly, there are new tools and more resources to draw on, and more business leaders are becoming attuned to the risks they face. To further equip the business with confidence, cybersecurity leaders must continue to engage on increasing organizations’ security IQ, making the case to be involved early and proactively, and continuing to build security and resiliency capabilities enabled by intelligent automation.
—Dillon Dieffenbach is a principal at Ernst & Young LLP and serves as the EY Americas Energy and Resources Cybersecurity Leader. He has more than 20 years of experience helping companies manage cybersecurity and technology risks across the enterprise. The views expressed are those of the author and do not necessarily reflect the views of Ernst & Young LLP or any other member firm of the global EY organization.