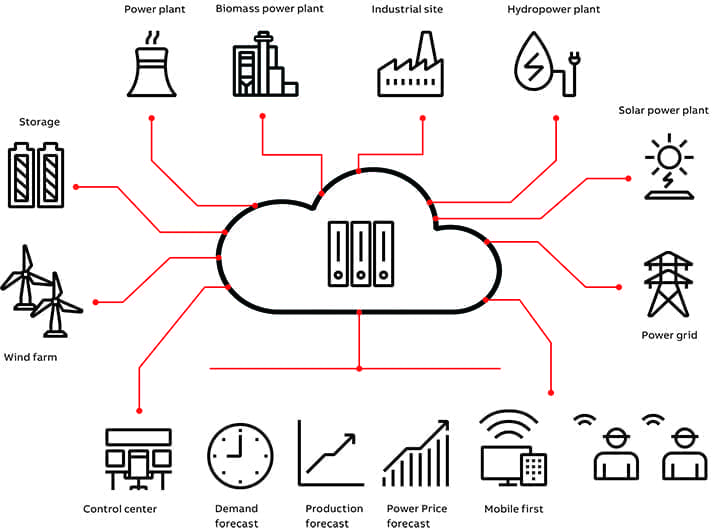
Virtual power plants are becoming a driving force in the power sector. This article explains how they enable utilities and aggregators to pool production from multiple plants and distributed sources,…
Power generation operations, plant siting, federal compliance, power plant finance, power generation saftey, power jobs

Virtual power plants are becoming a driving force in the power sector. This article explains how they enable utilities and aggregators to pool production from multiple plants and distributed sources,…
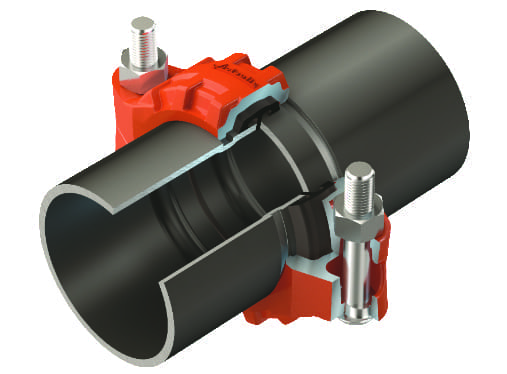
Up to 40% of a power plant’s piping is above-ground utility piping. Choosing the right joining method can help maximize efficiencies and have an outsized impact on overall project economics.…

The power generation industry is constantly evolving, with advanced technologies becoming more ubiquitous in power plants. Along with this evolution, instrumentation and control equipment continues to be key to a…
GE’s Advanced Gas Path technology will be installed on the two GE 9F.03 gas turbines powering the upcoming 718 MW plant. Power Plant to begin generating power in 2022. It…
YOKOHAMA, Japan, July 31, 2020 - (JCN Newswire) - Mitsubishi Hitachi Power Systems, Ltd. (MHPS), a part of Mitsubishi Heavy Industries (MHI) Group, announced on April 24, 2020, that it…
Chevron seeks to source more than 500 megawatts of renewable electricity for its operations OAKVILLE, ON, July 30, 2020 /PRNewswire/ - Chevron U.S.A Inc. (CUSA), a wholly owned subsidiary of Chevron…

Wind turbine maker Siemens Gamesa Renewable Energy (SGRE) has lowered its sales forecast for 2020, and the company said it expects the economic impact of COVID-19 will cut €1 billion…
Pilsen (30/7/2020) – The Pilsen steam turbine manufacturer will supply two 50MW steam turbines, including other parts of additional technology and equipment, for one of the most modern power generating…

GE Gas Power and Uniper have agreed to roll out a detailed decarbonization roadmap that may entail hydrogen-friendly upgrades to all GE gas turbines and compressors at the German generation…

Hecate Grid Awards 20 Megawatt Storage Contract for Southern California Project LAKE MARY, Fla., July 29, 2020 — Hecate Grid, an energy storage company formed by Hecate Energy and InfraRed…