By utilizing artificial intelligence (AI) and cloud computing, smart cybersecurity systems are helping to bolster the utility industry’s defenses. AI-powered cybersecurity is powerful because it enhances overall resilience to sophisticated cyber threats by providing real-time threat detection and response capabilities. And at a time when these threats are becoming more prolific and sophisticated, defenders need every advantage they can get.
COMMENTARY
What is smart cybersecurity? Smart cybersecurity tools, as compared to legacy or traditional cybersecurity, leverage AI, machine learning (ML), and automation to provide adaptive, proactive, and more efficient defense against evolving cyber threats. Unlike traditional security that relies on predefined rules to block known threats, smart systems, powered by multiple layers of AI, learn from data and previous security incidents to identify anomalous behavior and respond to new or unknown attacks in real-time. In short, smart cybersecurity has the power to learn and improve over time, just like human security analysts.
A few key characteristics of a smart cybersecurity defense approach include:
- Artificial intelligence and machine learning: AI and ML analyze vast data quickly to identify complex cyberattack patterns. ML models continuously learn to improve detection and counter emerging threats, such as zero-day vulnerabilities, at speeds that humans cannot match.
- Automation & adaptive networks: Automation does the heavy lifting on repetitive tasks, enables continuous network monitoring, and automatically updates security policies and defenses (firewalls, anti-virus, endpoints). That way, networks can instantly adjust security measures to threats, isolating compromised devices or blocking malicious traffic.
- Behavioral and identity analytics: Smart systems use AI to establish a baseline of normal activity, flagging deviations as potential threats to identify insider threats or compromised accounts that traditional, signature-based systems often miss.
What’s at Risk—And Why
Is all of this AI really necessary in today’s power infrastructure? The hard truth is that utility systems are at significant risk of cyberattacks due to the convergence of older, highly vulnerable legacy infrastructure with modern digital technologies. Joining these two worlds creates numerous entry points for attackers.
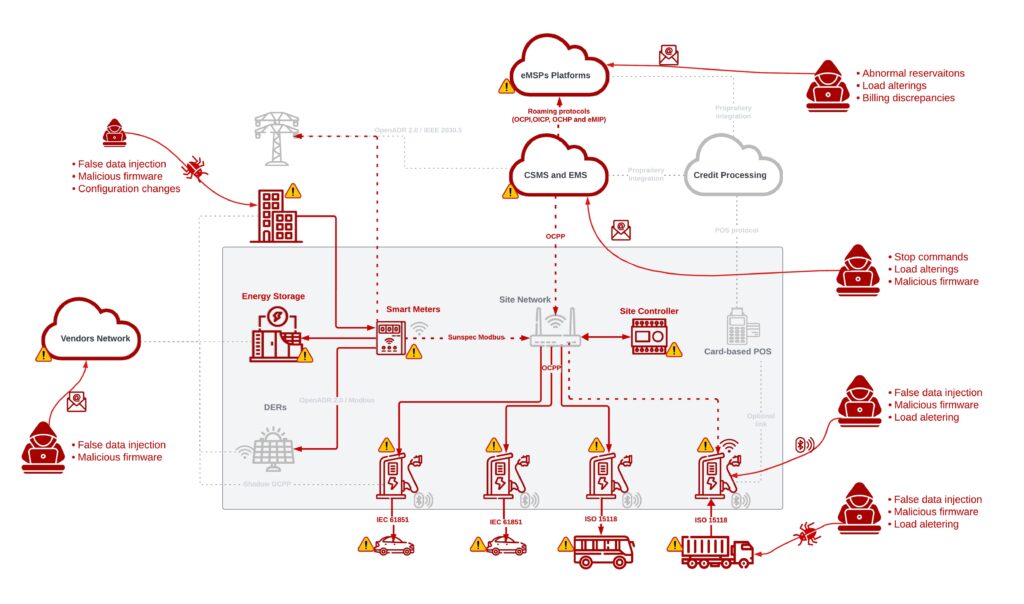
The adoption of smart grids, IoT devices (like smart meters and remote sensors), and the unification of OT with IT networks have expanded the utility industry’s attack surface. Previously isolated OT systems are now connected—and vulnerable. Moreover, utilities often rely on outdated infrastructure and operational systems with inadequate, unpatchable cybersecurity defenses, creating critical security gaps easily exploited by today’s AI-assisted threats.
Many utilities, particularly smaller ones, struggle with limited security budgets and a shortage of skilled cybersecurity professionals. This often results in understaffed security teams and a reactive, rather than proactive, approach to security.
The high value of the national power grid makes it a prime target for nation-states and cybercriminals. Recent attacks demonstrate how bad actors exploit vulnerabilities like default passwords for account takeovers, leading to service disruptions and data theft. Disrupting essential services, such as power and water, severely impacts public safety and the economy, making utilities lucrative ransomware targets often pressured into quick payment to restore operations.
For example, in September 2024, a water treatment facility in Arkansas City, Kansas, was targeted in a cyber incident, resulting in a temporary switch to manual operations. No service disruption occurred, but the event prompted a federal investigation. Multiple small water and wastewater plants in Texas (Hale Center, Muleshoe, Lockney, and Abernathy) were breached in January 2024 by a pro-Russian hacktivist group. Attackers posted videos showing them remotely interacting with SCADA systems, causing a water tank to overflow for about 45 minutes in Muleshoe. The vulnerabilities stemmed from internet-connected devices using a common vendor software that had default passwords.
Chinese state-sponsored “Volt Typhoon” hackers maintained persistent access for months within the network of Littleton, Massachusetts’ Electric Light & Water Department, as part of a broader espionage campaign targeting critical U.S. infrastructure (covered on 60 Minutes). The primary entry points often included outdated software, default credentials, or internet-exposed systems allowing remote critical infrastructure access.
How AI Safeguards the Smart Grid
AI systems analyze real-time and historical network data to quickly identify suspicious activities and anomalies. Today’s AI and ML can detect subtle behaviors, like unusual logins or indicators of compromise signaling malware. This enables faster detection and neutralization than legacy systems, often automating alert triage and containment while reducing human error.
AI helps utilities break down traditional silos between IT and OT networks. These modern security systems provide unified visibility and monitoring across the entire infrastructure, including control systems, smart meters, pipelines, and business applications, even the cloud, eliminating blind spots that attackers often exploit.
AI-powered security solutions offer a critical defense, particularly against vulnerabilities introduced by third-party vendors and supply chain partners, as demonstrated by incidents like the 2021 Colonial Pipeline ransomware attack.
By continuously monitoring and analyzing emerging global threats, threat intelligence systems and AI-powered security tools enable utilities to proactively identify vulnerabilities and quickly respond to potential attacks. Essentially, GenAI-powered security acts as a vigilant, “always on” security analyst, constantly patrolling the network and the broader environment for suspicious activity.
The Five Layers of AI Protecting the Smart Grid
For utility operators to fully capitalize on AI-enhanced security, they must implement a multi-layered defense strategy that includes architectural safeguards specifically engineered for the AI era.
This includes:
- First-generation AI and deep learning ML that provide predictive analytics.
- Generative AI, such as copilots or personal assistants, to assist defenders.
- Graph ML to help correlate security alerts and events automatically, surfacing attacks undetectable to the human eye.
- Hyperautomation, the evolution of Security Orchestration, Automation, and Response (SOAR) technology, to enable the execution of security operations tasks with minimal reduced human involvement.
- Agentic AI, enabling lean security teams to transition from reactive to proactive defense with minimal human supervision by operating with goal-driven autonomy to prioritize threats and triage alerts.
Regardless of size and scope, a multi-layered AI approach to network detection and response significantly enhances the speed, scale, and efficiency of Security Operations Center (SOC) environments. By implementing multi-layered AI, security professionals can focus on more intricate tasks that keep the smart grid protected.
Final Thoughts
The utility industry faces an escalating and sophisticated cyber threat landscape, made more vulnerable by the unification of legacy infrastructure and modern digital technologies. To effectively meet this challenge, traditional security measures are no longer sufficient. The implementation of smart, AI-powered cybersecurity systems—featuring multiple layers of technologies like Generative AI, Graph ML, Hyperautomation, and Agentic AI—is not just an enhancement, but a critical necessity. This multi-layered approach provides utilities with unified visibility, real-time threat detection and response, and the capability to transition from a reactive to a proactive defense posture.
By embracing these architectural safeguards, security teams can significantly enhance the speed, scale, and efficiency of their Security Operations Center (SOC) environments, ensuring the continuous protection and resilience of the nation’s critical power infrastructure for the AI era and beyond.
—Subo Guha serves as senior vice president of Product Management at Stellar Cyber, where he leads the development of the company’s award-winning, AI-driven Open XDR solutions.