Introduction to NERC CIP Version 5
Even if your generating facility was exempt from previous versions of NERC’s Critical Infrastructure Protection standards, the latest version dramatically steps up the number of facilities encompassed, so the odds are high that your plant will be within its scope.
The North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) standards Version 5 represents the first major change in requirements and approach since its predecessor, Urgent Action Standard 1200, was approved more than a decade ago. The most notable change is the tiered impact rating system, which classifies bulk electric system (BES) Cyber Systems into High, Medium, and Low categories. This approach results in all cyber assets that could impact BES Facilities being in scope for the CIP standards.
Because the standards become effective less than two years from now (Table 1) and cover so many more facilities than previous standards (in version 5, all generating plants that meet the BES definition will be in scope), now is the time to become thoroughly familiar with the latest version to ensure the reliability of the system we all depend upon.
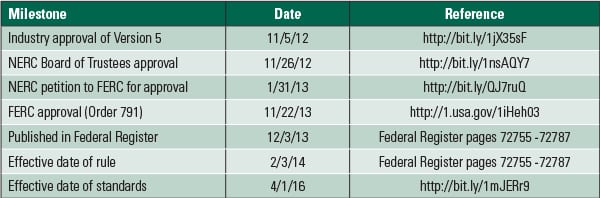 |
| Table 1. NERC CIP 5 milestones. Source: EnergySec |
In previous CIP versions (Version 3 being the most recent, as Version 4 was effectively omitted), only those generation facilities determined to be Critical Assets by their owner/operators were required to comply with the standards. Even then, a wide range of assets were excluded simply by avoiding the use of routable communication protocols. The result was that a broad swath of generation facilities had virtually no compliance obligations under the CIP standards.
Version 5’s tiered classification brings all BES generating facilities into scope for at least some requirements. A new “bright line” approach to identifying cyber assets that qualify for protection under the CIP standards ensures that most systems used in the operation of any BES generation facility will be in scope for at least some requirements. Cyber assets meeting certain criteria will be grouped into systems and assigned a High, Medium, or Low impact rating based upon the characteristics of the facility they support. For example, BES Cyber Systems at plants larger than 1,500 MW may receive a Medium impact rating, while most black-start units will be Low impact. All such systems, referred to officially as BES Cyber Systems, will be assigned at least a Low impact rating and will be required to comply with at least a portion of the requirements.
There is a single requirement for Low-impact BES Cyber Systems, but that single requirement has a broad scope. Generators are required to develop and implement security policies that address four specific areas of concern: security awareness, physical security, remote access connections, and incident response. The rest of this article focuses on these basic considerations that apply to all BES Cyber Systems.
The importance of the implementation requirement cannot be ignored. Simply creating policies will not be sufficient for compliance. Policies must be implemented through the deployment of processes, procedures, and controls that meet the objectives described in the written policies. Significant flexibility is provided with respect to the design of controls, but the stated objectives must be met, and generators will be audited against what has been implemented.
Security Awareness
The responsibility for security falls, to some extent, on each and every individual within an organization. Security attacks often take advantage of individuals who ignore, or are unaware of, basic security precautions.
For example, the most effective (and commonly used) initial attack vector into an organization is email. (See also “Just Hop on the Bus, Gus: 13 Ways to Hack a Power Plant” in this issue.) Attackers send messages designed to convince an individual to open an attachment or click a link. Upon doing so, security vulnerabilities can be exploited, giving control of the victim’s machine to the attacker, and with it, an entry point to an organization’s internal computer networks, including the generation control systems.
To strengthen security, CIP Version 5 requires that programs be implemented to promote awareness of security risks and reinforce secure precautions that should be taken. The development and implementation of such a program is one of the four required protections for Low-impact systems.
A security awareness program should be broadly applicable across an organization. Although it is not necessary to track awareness messages to ensure that each individual receives every message, the program should be developed and executed in a manner that makes it likely that all individuals in the organization will regularly receive such messages.
Many such general security awareness messages are appropriate for general audiences across an organization. For example, tips on the selection and use of strong passwords help ensure compliance with password policies and reduce the likelihood of passwords being guessed. Another common topic is email security. General awareness of the types of risks posed by email, including how to recognize the attacks that are often sent via email, can substantially reduce the probability, or at least the frequency, of successful intrusions via this method.
Physical Security
The second area of concern that requires policy action is physical security, a control that is critical to the overall security of any digital system. If an attacker can gain physical access to a computer system or other electronic device, full compromise of the device is nearly assured. Likewise, physical access to network ports or communication media can allow an attacker to intercept, interfere with, or even inject messages onto a network. In control environments, this can have catastrophic consequences.
Access to BES Cyber Systems and associated networks should be restricted to only those personnel who require access for the performance of their jobs. Physical security controls must be implemented to enforce access restrictions and to allow for the detection of unauthorized access. Such controls can be preventive, or detective. Preventive controls are designed to prevent unauthorized access from occurring. Examples are fences, walls, doors, and locked cabinets. Detective controls are designed to emphasize the detection of unauthorized access and would activate an appropriate response procedure. Examples include alarm systems, video surveillance, and guard patrols.
Remote Access Connections
The third area of concern is remote electronic access. The single greatest reason that cybersecurity is such a significant issue today is the tremendous increase in connectivity of critical systems and the global reach of the Internet. Any system that is connected to the Internet—even indirectly through multiple other systems or networks, and even if a plant worker is unaware of those connections—has some risk of compromise by motivated parties.
Although attacks can also be conducted locally by individuals that gain physical access, the near ubiquity of network connectivity has enabled attacks that many engineers would find inconceivable. Remote connectivity to systems increases the pool of potential attackers by orders of magnitude, while simultaneously reducing the cost, difficulty, and risk an attacker must overcome.
Remote connections come in many forms and are used for many purposes. Internet access, dialup, serial connections, wide area networking, and wireless are examples. These may exist for many legitimate business purposes including employee remote access, vendor support, operational control, and business partner communications. A good CIP Version 5 process requires that such connections be controlled and monitored to reduce the likelihood of successful intrusions and to detect and quickly respond to those that do occur.
Incident Response
Despite the best efforts of organizations to protect their cyber assets, successful attacks are likely to happen, at least occasionally. Organizations must be prepared to respond appropriately to such events not only because the potential financial costs of equipment malfunctions or worse can be enormous but also because the longer a security breach is unaddressed, the greater the potential damage not only to an individual facility but also to other facilities and the interconnected grid.
Incident response plans should be established to effectively handle intrusions and other cybersecurity events. These should include the identification and training of personnel who will be responsible for the initial response, investigation, and containment, as well as notification and escalation procedures to senior management, legal, and communications staff.
Plans should include provisions for external notification of law enforcement and other appropriate agencies or organizations such as the Department of Homeland Security’s Industrial Control Systems Cyber Emergency Response Team (ICS-CERT), the Electricity Sector Information Sharing and Analysis Center (ES-ISAC), and/or other state and local authorities. Plans should also allow for the involvement of commercial incident response and forensic investigation specialists, as needed.
Recent Developments
Although there is a dramatic expansion of systems that are in scope for NERC CIP Version 5, there is still room for improvement. In its order approving Version 5 of the CIP standards, the Federal Energy Regulatory Commission (FERC) raised concerns regarding the lack of specific requirements for Low-impact systems.
Although the standard requires that policies be developed and implemented in four key areas, there are no specific requirements, and no criteria against which to measure the effectiveness of controls that are actually put in place. The lack of specific requirements leaves FERC with little oversight or assurance that security risks will be adequately addressed.
To correct this situation, FERC has directed NERC to either develop new requirements for Low-impact BES Cyber Systems or develop “objective criteria” that can be used to evaluate the effectiveness of the controls that are deployed.
Although it is not yet known which approach will be taken or what potential specific controls may be required, the objectives are clear, as is the need. Organizations should develop and deploy controls that provide prudent protections in the four identified areas of concern. Although some adjustments may need to be made based on the actual requirements developed by NERC, those organizations that have worked proactively to address these areas of risk will be both more secure, and better positioned for compliance.
The concern over cybersecurity risks to critical infrastructure, of which power generation is a significant element, is unlikely to wane in the foreseeable future. In fact, the issue is receiving increasing scrutiny from the federal government and, recently, state utility commissions and legislatures. The expectation that critical infrastructure operators will proactively and effectively address cyber risks is increasing.
Additionally, with respect to the NERC CIP standards, there is an active effort to shift the focus of audit and enforcement away from a strict measurement against specific requirements toward a qualitative assessment of internal controls. This move will reinforce the need for holistic approaches that emphasize real security rather than mere compliance.
Compliance requirements can be an effective catalyst to kickstart cybersecurity efforts, but if they remain the only focus, long-term success is unlikely. Holistic efforts that view cybersecurity as a means to compliance, rather than assuming compliance is the basis for security, are the only effective way to address both concerns now and into the future. ■
— Steven Parker, CISA, CISSP is president and a founding director of Energy Sector Security Consortium (EnergySec). He has been engaged in electricity sector critical infrastructure protection for more than a decade, including eight years at PacifiCorp. He was also part of the team that established the NERC CIP audit program at the Western Electricity Coordinating Council.