OT Cybersecurity vs. IT Cybersecurity: Different Worlds, Different Approaches
In the carpeted world of IT cybersecurity, it’s about the data. Securing confidential data is the highest priority because data breaches are expensive and embarrassing, damaging to organizations and harmful to individual victims.
Reflecting that priority, IT security generally applies the “CIA Triad”, which assigns the highest priority to Confidentiality, keeping data private. Integrity, keeping data secure, accurate, and authentic is next. Then, Availability, making sure data is available to authorized users when needed.
That last one, Availability, is a problem, since many attackers simply impersonate authorized users through any number of tricks, and thus gain access.
In the grittier plant-floor and in-the-field world of operational technology (OT) cybersecurity, the imperative is operations. Complicating matters, many OT networks are a patchwork of legacy and new systems rather than the standardized, modern systems of many IT networks.
Attacks on operational technology that shut down production can be costly, especially if they happen near the top of the supply chain and cascade downward to other businesses. But they can also be dangerous. Beyond just grinding to a halt, malfunctioning equipment can injure workers, spew pollutants, ignite, explode, or suffer any number of catastrophes.
So, in OT security, the “AIC Triad” presides. Availability is prioritized because the equipment must be available to the people who need it, doing what it needs to do. There can be no unplanned interruptions or risks to human safety.
That’s where OT zero trust comes in.
So What is Zero Trust in Terms of OT?
OT zero trust means never trust, always verify. Assume everyone who’s about to plug a flash drive into your equipment could be carrying malware. Assume every software download or piece of equipment is infected with a bug, even if you downloaded the update from the vendor or took the equipment brand-new from the box.
Because those are indeed some of the ways operational technology has become infected. Even trusted and well-meaning employees have carried malware on-site in an unsecured USB drive. Trusted third-party technicians have come with equipment, unaware that it’s infected, and connected it to a customer’s system. And yes, malware has even been hidden in otherwise legitimate software updates and newly manufactured equipment, unknown to everyone except the attackers who hid it there.
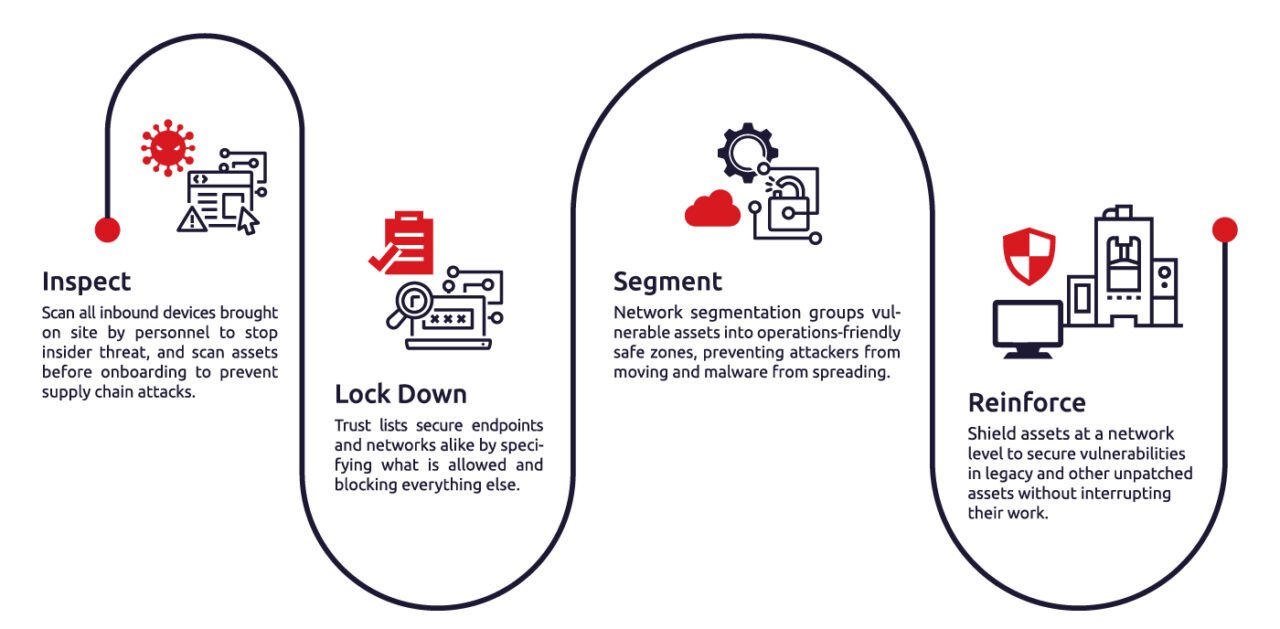
Inspect Everything. No Exceptions.
As we said, zero trust means assuming nothing is safe, everything’s infected, and even the well-intentioned may be carrying something (and, of course, not everyone is well-intentioned). So OT zero trust must begin the moment the device enters the work site, before interfacing with anything.
If industry regulations block scanning software from being installed on standalone systems, a portable, handheld scanning device can be used very effectively to proactively inspect and scan devices for malware and conduct any cleanup.
- Strive for full visibility. Take a full inventory of all assets.
- Scan all inbound devices brought on-site by anyone, including vendors and staff.
- Make sure all work sites have a checkpoint that’s equipped to quickly conduct scans, remove malware, and log the results.
- Conduct scans of newly arriving equipment.
- Scan all downloaded software, even from trusted sources.
Lock Down Endpoints With a Trust List
With a trust list, you secure endpoints and networks by clearing and specifying what’s allowed. If it’s not on the list, it doesn’t run. It gets blocked.
The challenge is the scattershot makeup of many OT environments, with assets from different vendors, with modern and legacy equipment functioning side by side. Each needs defenses that can accommodate its needs and purpose — without disrupting availability.
- For fixed-use and legacy systems, deploy a straightforward trust list that only allows work-necessary applications to run. Unapproved updates from vendors and malicious files are automatically blocked.
- Modern endpoints are more difficult without interrupting availability. Try filtering based on a library of verified OT applications and licenses. And modern devices may need next-gen antivirus that incorporates machine learning.
Segment the Network Into Safe Zones
By segmenting the network into “operations-friendly safe zones,” you can limit an attacker’s movements and keep malware from spreading. Appliances such as intrusion prevention systems (IPS) and firewalls are the tools of choice.
- Create safe zones based on which assets do or don’t need to communicate.
- By segmenting the network, you can isolate or aggregate vulnerable assets to escape zero-day attacks, where hackers exploit a vulnerability unknown to the developers.
Reinforce: Shield OT Assets Until a Patch Arrives
Patching is never simple in OT environments. Is the patch available? Compatible? Are you even allowed to patch the asset? How does it impact production? Until a vendor-supplied patch is available and tested, and the time is right to install it, shielding OT assets can reduce the risk, providing security and continued operations at the same time.
- For technicians, MTTP (mean time to patch) is less of a concern.
- Assets can be secured regardless of patch status with virtual patching.
- The OT-native IPS and firewalls you’ll use have rules specified to repel attacks without forced updates, reboots, or production downtime.
Keep the operation running
Take a proactive approach to secure your operations and get started on your journey to OT zero trust. Please download your free copy of The OT Zero Trust Handbook.
About the Author:

Austen Byers, Technical Director, Americas at TXOne Networks. Austen leads the company’s efforts in providing design, architecture, and engineering technical direction and leadership. With more than 10 years in the cybersecurity space, Austen is a sought-after subject-matter expert to provide insight into the state of industrial cybersecurity, the intricacies of OT breaches, and providing strategies to help organizations keep their assets and environments safe.
About TXOne Networks
TXOne Networks is the leader of OT Zero Trust offering cybersecurity solutions that ensure the reliability and safety of ICS and OT environments through the OT zero trust methodology. Working together with leading manufacturers and critical infrastructure operators, TXOne develops practical, operations-friendly approaches to cyber defense. TXOne offers both network- and endpoint-based solutions that integrate with the layered arrangements and varied assets common to work sites, providing real-time, defense-in-depth cybersecurity to both mission-critical devices and the OT network. Learn more at www.txone.com.