Cyberattack Vulnerabilities of Modern Power Systems
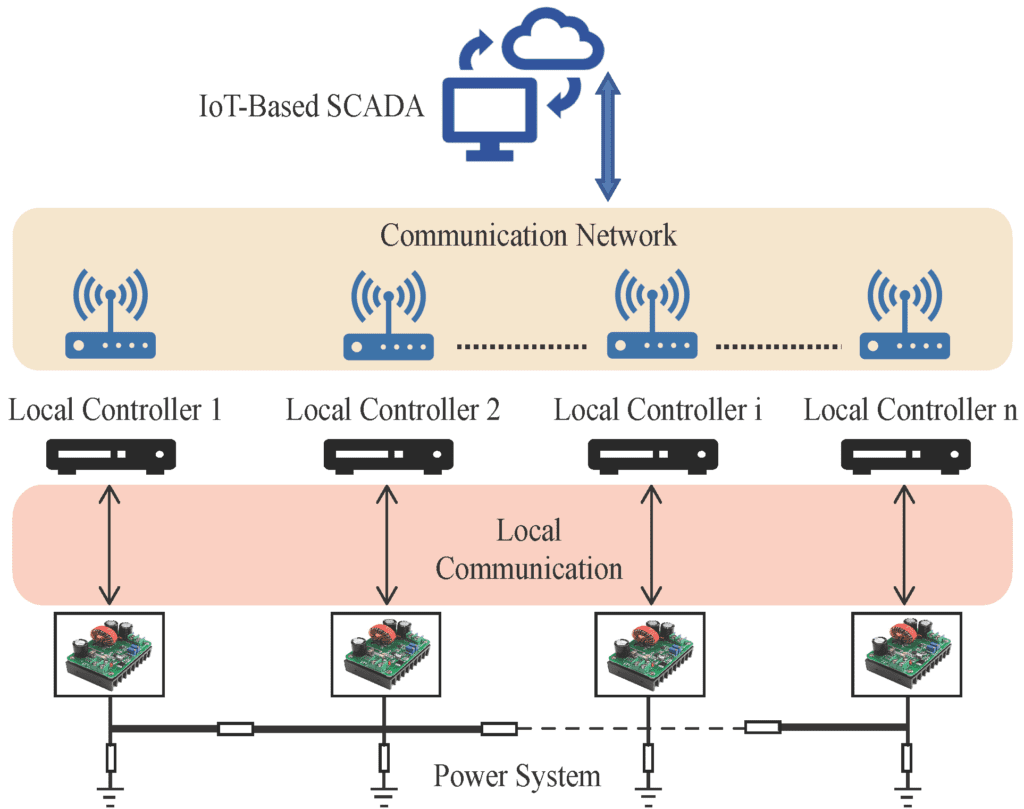
Supervisory control and data acquisition (SCADA) is crucial to contemporary power systems and is widely used in industry and defense. SCADA are computer-based systems that are used to centrally control, monitor, and analyze activities in industries and power systems. This entails real-time communication over a communication network between a central entity and the local controllers in the field, such as programmable logic controllers (PLCs), embedded controllers, and remote terminal units (RTUs), as depicted in Figure 1. This architecture is widely employed in the production of hydroelectricity, wind energy, and solar energy.
COMMENTARY
The operator can visualize the data through a human-machine-interface (HMI). In a SCADA architecture, the local controllers can also communicate with sensors, and actuators (power devices). This data is then transmitted to a central computer over a communication network, where it is processed, analyzed, and displayed through HMI to present a comprehensive field picture to the operator. The operator can also initiate control actions based on the data. SCADA systems are also vulnerable to cyberattacks as these are dependent upon information exchange over the communication networks and the local communication.
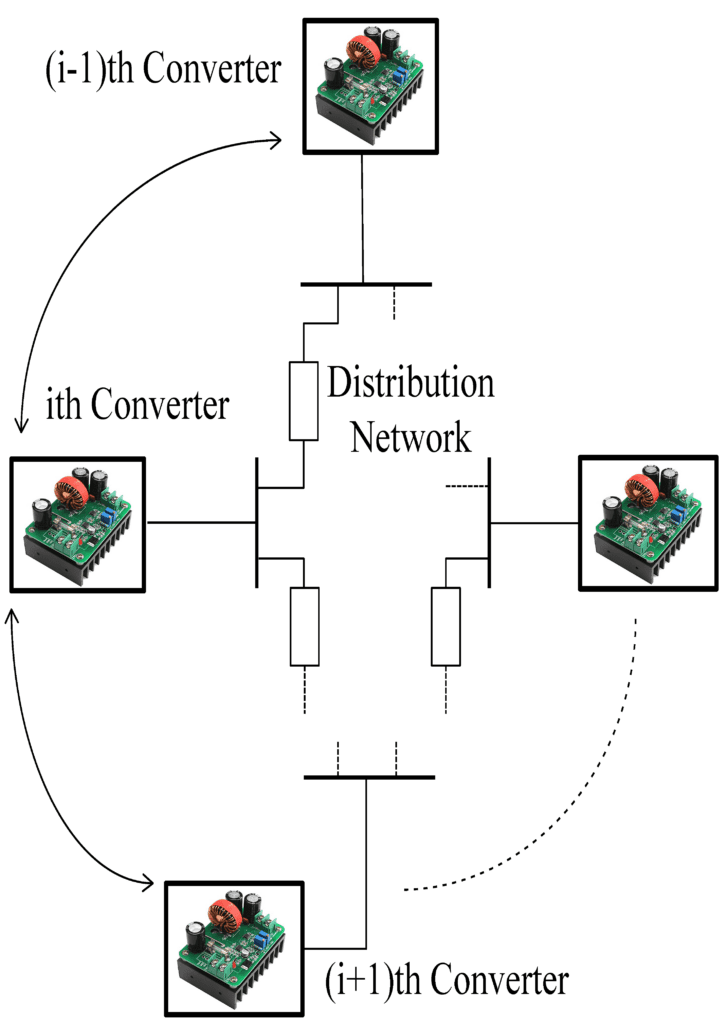
Another type of modern power system is distributed cooperative control, where a power device’s controller action (such as a converter) depends on the data from nearby devices on the communication network. Due to complex interactions between the physical layer (consisting of converters, loads, and the power distribution network) and the cyber layer (consisting of software-based controllers and the communication network), such systems with distributed cooperative control have evolved into cyber-physical systems (CPS) or IoT-based systems.
In such a control strategy the control signal for a given converter depends on the information shared among converters neighboring on a communication graph to ensure that all the converters reach consensus on quantities of interest. As shown in Figure 2, this information exchange takes place among the ithconverter and its neighbors, i.e., (i + 1)th and (i – 1)th converters. This control scheme achieves two objectives, proportional load sharing among the converters, depending upon their respective power ratings, and global voltage regulation over the distribution bus.
Such distributed control architectures are preferred over the centralized control architectures as the latter require high communication bandwidth and expose a single point of failure. However, the distributed cooperative controllers are also vulnerable to cyber intrusion by adversaries due to their dependency on communication networks or IoT devices. Absence of a central controller can also lead to a limited global situational awareness that makes such power systems susceptible to hostile cyber scenarios. In addition, the distortion effects of the physical anomalies, such as faults, may be propagated to other devices due to inherent cooperative control protocols.
In December 2015, Ukraine’s power system collapsed, knocking out electricity to thousands of homes and buildings as a result of a cyberattack brought on by the malware known as BlackEnergy that infected computers in the control center. Cyberattacks may cause significant damage to highly sensitive and mission critical equipment in defense installations and civil infrastructure. In the case of power electronics-intensive microgrids, the aftereffects of such cyberattacks are even more detrimental due to comparatively weaker and fragile distribution grid, highly dynamic source and load profiles, and meager generational inertia.
Due to these vulnerabilities of the modern power systems, an effective cyberattack detection mechanism is required to provide a real-time picture about the hostile cyber scenario. Recently, extensive research has been conducted to make modern power systems more resilient against such cyber intrusions. The research community has proposed various resilient mechanisms based on consensus-based cooperative control, artificial intelligence (AI), adaptive control, formal verification, to mention a few. AI-based detection and classification techniques can provide such first-hand knowledge about a cyberattack and the operator can initiate a mitigation action to defend against adversaries. As research in AI is evolving at a great pace, AI-based techniques can be applied for resilient control and cyber-security of modern power systems. Such techniques are based on machine learning and neural networks.
—Omar A. Beg is an Assistant Professor and Coordinator of Electrical Engineering at The University of Texas Permian Basin. His aim is to promote research and education on smart grids and resilient power systems.