Securing Industrial Control Systems: A Holistic Defense-In-Depth Approach
Defense-in-depth is a concept that is already widely deployed by many organizations within their IT infrastructures. However, many organizations do not apply it to their industrial control system (ICS) operations, owing mostly to obscure protocols. But as IT and ICS architectures converge and high-profile cybersecurity incidents mount, a robust, holistic defense-in-depth solution may be essential to render systems unattractive to would-be attackers.
Critical infrastructure is infused with proprietary protocols and software, air-gapped networks, and robust physical security systems—an amalgam that effectuated the notion of “security by obscurity” in the industrial control systems (ICS) community. Still, business needs eventually necessitated the convergence of information technology (IT) and ICS architectures. Although this seems like a match made in heaven, from an IT perspective, designing visibility and control into a system that inherently lacks them is a challenge that can be painful.
However, IT’s “defense-in-depth” security approach could be effective for ICS security. After all, this strategy employs a holistic approach to protect all assets—people, technology, operations, and adversarial awareness—while considering its interconnections and dependencies to provide effective layers of monitoring and protection based on exposure to cybersecurity risks (Figure 1).
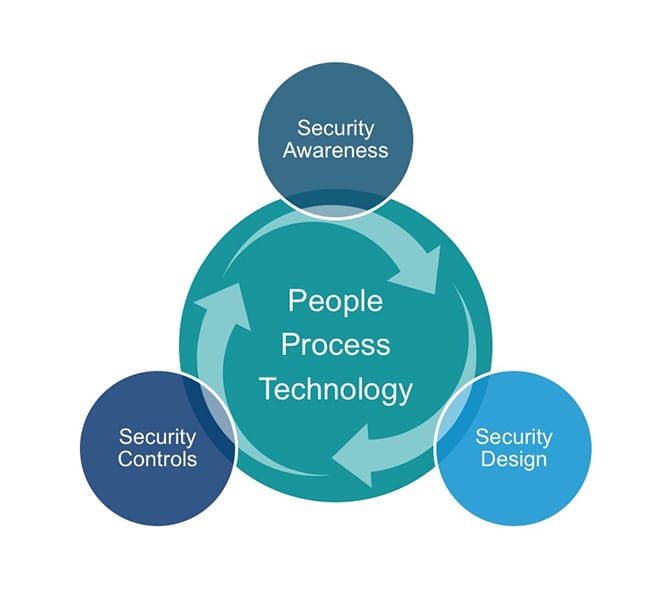
The following highlights plausible best-practices for securing ICS environments using a defense-in-depth approach (Figure 2).
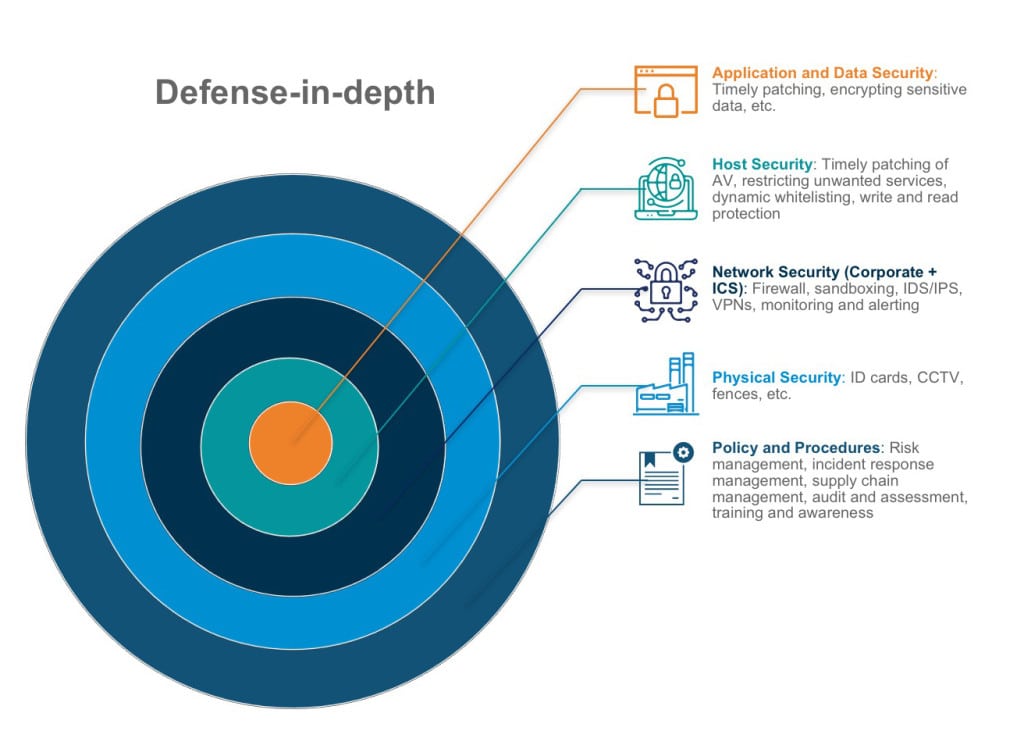
Policy, Procedures, and Training
An effective ICS security program depends on the willingness of the operations staff and management to accept security as an enabler for all computer-oriented activities, as well as their ability to apply controls from a standpoint of acceptable risk.
With this in mind, organizational leadership must clearly define and communicate cyber security roles, responsibilities, expectations for performance, and authorities for managers, system administrators, and users through training programs and policies, while holding individuals accountable for their performance. This minimizes the likelihood of organizational personnel inadvertently disclosing sensitive information regarding supervisory control and data acquisition (SCADA) system design, operations, or security controls. Likewise, good management practices in handling delicate situations, recognizing and rewarding employees, and looking after their well-being can help diffuse potential insider threats.
Risk Management
Designing an effective ICS security architecture requires a risk model that maps functional requirements of these complex systems and provides a holistic image of potential real-world consequences. A thorough risk analysis procedure consists of identifying all assets (including software, network elements, and people) in the organization, as well as risk drivers or threats such as disgruntled employees, terrorists, hostile countries, and more.
Establishing a “Red Team” to identify potential attack scenarios and evaluate system vulnerabilities can help detect plausible intrusion methods, which should be evaluated as risks and categorized based on their likelihood of occurrence and impact to the organization. Note that actionable policies and procedures, along with monitoring and feedback, should be part of the risk management program. Periodic review is essential to stay current with evolving threat landscapes.
Vendor and Supply Chain Management
Organizations regularly employ contractors and third-party vendors who do not have uniform cybersecurity policies and practices. This creates exploitable weaknesses in the operations chain. Therefore, it is recommended that third-party requests be reviewed by IT—as well as legal and other relevant departments—with proper documentation. Documentation should be accompanied by regularly scheduled compliance reviews/revalidation, all based on assessed risks while confining intellectual property access to a need-to-know basis only. Likewise, rigid guidelines for evaluating purchase of new SCADA devices must be established.
Incident Response Management
A comprehensive cyber incident response plan should include both proactive (to prevent incidents) and reactive measures (to detect and manage an incident). Therefore, it is recommended to establish a 24/7 incident monitoring program with the ability to detect threats to the ICS network. Having a comprehensive response plan (such as isolation strategies and disabling affected accounts) when adversarial activity is detected is also important. As critical is having a restoration plan—including establishing system backups (redundant hardware and fault tolerant systems)—and disaster recovery plans (fallback mechanisms).
Audit and Assess
Auditing eliminates the “paths of least resistance” that an attacker could exploit. This involves technical audits of SCADA devices and networks, physical security surveys, and assessments of all remote sites connected to the SCADA network. This will identify security concerns while maintaining compliance with standards such as: NIST-80053, NERC CIP, French ANSSI, CIDX/ACC, AGA 12, API, ISA/IEC 62443, CPNI, CPNI, ISO 27001, and others.
Compliance with standards/regulations does not guarantee continuous security, but it does provide a snapshot of required controls at a point-in-time. Considering numerous factors affect security of a system throughout its life cycle, periodic testing and verification is important in achieving optimal security.
Physical Security
Physical considerations typically refer to a ringed architecture of layered security measures that restricts access to users to fulfill their duties only. Some measures include authentication for physical access such as key cards and biometrics, facility monitoring (cameras and motion detectors), perimeter defense (fences and anti-vehicle ditches), and visitor escort procedures.
Network Management
Securing ICS against modern threats requires well-planned and implemented strategies to give network defense teams a chance to quickly and effectively detect, counter, and expel an adversary. Therefore, it is recommended to:
- Document network architecture and identify critical systems, connections to SCADA networks, and host-to-host communications paths. Evaluate the risks and disconnect items that aren’t required.
- Physically separate corporate and control domains. Ensure isolation of ICS networks from untrusted networks and allow real-time connectivity to external networks only if there is a defined business requirement or control function.
- Logically segment networks and isolate critical parts of systems. Demilitarized zones (DMZ) and data warehousing provide a secure buffer zone where services and data can be shared and secure transfer of data from the SCADA network to business networks can be ensured.
- Deploy network access control and manage authentication (preferably two-factor or more) by requiring separate credentials for corporate and control network zones, and store these in separate trust stores. Never share active directories, RSA ACE servers, or other trust stores between corporate and control networks.
- Require any remote access to be operator-controlled and time-limited. Firewalls, virtual private networks, callback (for dial-up), multi-factor authentication, user access control, and intrusion detection can provide “secure” remote access to computer networks.
- Engage network monitoring tools and complement them by enabling logging on all systems. Regularly audit system logs to detect suspicious activity as soon as possible.
- Take measures to avoid “watering hole” attacks. Use a web domain name (DNS) reputation system. Get updates from authenticated vendor sites. Validate the authenticity of downloads. Insist vendors digitally sign updates and publish hashes via an out-of-bound communications path, and require they use these to authenticate.
- Lock down all unused ports, services on routers, switches, and network daemons. Change all default configurations and passwords.
- Deploy deception networks to boost the odds of finding an adversary early and mitigating overall damage.
Host Management
Asset inventory is an accurate baseline for identifying necessary security controls. Having identified the assets, lock down all unused ports and services on the host, and restrict privileges to only those needed. Also, manage authentication (preferably multi-factor) with secure password policies—stressing length over complexity—which should be unique and changed at least every 90 days. Harden the host by methods that include application dynamic whitelisting, memory protection, write protection, and read protection.
Implement change management policies and procedures for protection against improper modifications prior to, during, and after commissioning. Have a configuration/patch management program centered on the safe importation and implementation of trusted patches. Monitor host activity and alert unauthorized changes.
Application and Data Management
Applications and data are critical elements of ICS environments. Avoid embedding hard-coded passwords in ICS applications. Also, demand that vendors disclose any backdoors or vendor interfaces to your SCADA systems and expect them to provide systems that are capable of being secured.
Conduct an initial assessment (static and dynamic analysis) and ensure compatibility of the application with the host operating system before deploying it. Restrict access to the application and data only to intended users. Finally, it is recommended to use cryptographic controls and data sanitation techniques to maintain the integrity and authenticity of the data collected.

No environment is 100% secure. A threat-actor, through intent, capability, and opportunity, will always pose a threat to an ICS network by trying to compromise an organization’s systems through its operations, personnel, technology, and other vulnerabilities. Implementing the strategies and controls presented in this article can greatly improve the security posture of ICS.
This said, the determination of a security control is context-based, and there might arise a situation where ICSs have functional or operational properties that disallow application of a security control. In such cases, it is recommended to identify, assess, and implement necessary compensatory controls and ensure the SCADA security policies and standards complement the organization. IT security policies should also evolve to meet changing threat profiles and be scalable to accommodate different standards and regulations.
It needs to be foremost in everyone’s mind that in the SCADA world, availability, reliability, and stability are the most important criteria to be considered.
—Vishruta Rudresh is senior cybersecurity researcher at Kudelski Security www.kudelskisecurity.com.
