Though increasingly serious cybersecurity threats loom, nearly two-thirds of U.S. industrial control system (ICS) vulnerabilities identified in 2017 could cause severe operational impact if exploited, cybersecurity firm Dragos Inc. warned in a series of reports published March 1.
The reports, which cover ICS vulnerabilities, ICS threats, and reactions to existing threats, draw a dire picture of the current state of ICS cybersecurity.
In one report, Reid Wightman, Dragos senior vulnerability analyst, notes that public disclosures issued in 2017 fail to adequately define the industrial impact of vulnerabilities. Most provided no alternative guidance beyond “patch” or recommendations to use secure networks, and the firm concluded that public reporting will need a “huge improvement.”
Another report, authored by Joe Slowik, a Dragos senior threat analyst, noted that 2017 was a defining year in ICS security. Last year alone, two major and unique disruptive attackers were revealed, five distinct activity groups targeting ICS networks were identified, and several large-scale IT infection events with ICS implications occurred. But according to Dragos, 2017 was only “scratching the surface,” and the firm expects much more activity in 2018 and beyond.
A third report authored by Ben Miller, director of Dragos’ Threat Operations Center, says that industrial attacks are being commoditized through new malware with real-world impacts to reliability and safety. Miller cautions that that protections alone cannot be enough, and more proactive measures will be imperative.
Vulnerability Reports Are Too Vague
According to Wightman, on average, organizations disclosed 14 vulnerabilities monthly through 2017. The bulk of these bore high risks: 71% of all 2017 ICS-related vulnerabilities could result in a loss of view, or the inability to monitor or read a system state, while 63% could result in a loss of control.
Yet 64% of 2017 ICS-related vulnerability patches don’t fully eliminate risks because components were “insecure by design,” Wightman noted. The bulk of vulnerabilities apply late in the kill-chain, making them toothless in gaining an initial foothold. “If these vulnerabilities are exploited, it is likely the adversary has been active in the network for some time and already pivoted through various other systems,” he warned.
The trouble is rooted in the nature of ICS vulnerability assessments, which are “frightfully inadequate” and “woefully uninformed” in providing asset owners and operators with meaningful guidance, he said. Advisories must provide reasonable effective alternative options. Even if these are not applicable to all users, they could help some, Wightman’s report concludes.
Advice should include specific ports and services to restrict or monitor to reduce risk and impact from an attack, or specific system-hardening recommendations to better defend systems from local exploitation. Advisories should also adopt ICS-specific metrics to better inform users of operational risks, he said.
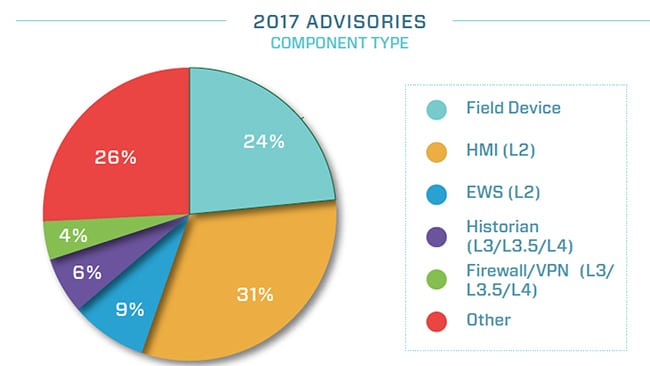
Another shortcoming is that industrial-focused advisories tend to focus predominantly on hardware and field devices, and not as much on network perimeter and entry points to ICS networks. “Nearly 66% of advisories cover human machine interface (HMI), engineering workstations (EWS), and field device components; historians, OPC servers, and analytics services all provide cross-domain access between corporate and ICS networks,” he said (Figure 1). However, mitigating vulnerabilities in these components does little to reduce overall risk, “because the components themselves are insecure by design.” A better approach would be to increase scrutiny on cross-domain devices and applications where research outcomes will lead to a stronger first layer of defense.
- Vulnerable components. About 64% of the 2017 ICS-related vulnerabilities surveyed by cybersecurity firm Dragos in 2017 impacted interior control system components (HMI, EWS, or controllers), while 26% were reported in field devices (PLCs, RTUs, and other controllers that directly read and operate the physical process). The firm also found that the majority of 2017 vulnerabilities were sourced from hardware or software that was procured at costs—as opposed to in free or “demo” software. Courtesy: Dragos
Patch production is also problematic, Wightman said, pointing out that major vendors have released patch-sets that triggered failures in end-user systems. A patch management program must begin with developing a “test” or “development” control systems network, which contains samples of the actual plant’s critical systems. “This allows for proper testing of patches, and minimizes the risk of outage of any critical plant systems,” he said.
Threats Are on the Rise
Meanwhile, according to Slowik, 2017 was a “watershed” year in ICS security largely due to the discovery of new capabilities and a significant increase in ICS threat activity groups.
Before last year, only three families of ICS-specific malware were known: STUXNET, discovered before 2010, BLACKENERGY 2, discovered in 2012, and HAVEX, which emerged in 2013. Over 2017, two new samples emerged: TRISIS and CRASHOVERRIDE. While the impact of these adversaries cannot be understated, Slowik said, Dragos is “confident” that additional unknown events have occurred.
“Both of these samples led to industry firsts. CRASHOVERRIDE was the first malware to ever specifically target and disrupt electric grid operations and led to operational outages in Kiev, Ukraine in 2016 (although it was not definitively discovered until 2017),” he said “TRISIS is the first malware to ever specifically target and disrupt safety instrumented systems (SIS), and is the first malware to ever specifically target, or accept as a potential consequence, the loss of human life.”
Slowik pointed out that while numerous incidental infections occur in industrial networks on a regular basis, ICS-specific or ICS-tailored malware is rarer. However, the emergence of the two new malware samples is an ominous sign for industrial systems, which are likely to see operational losses and safety events into 2018 and into the foreseeable future, he suggested.
“There are now five current, active groups targeting ICS systems—far more than our current biases with respect to the skill, dedication, and resources required for ICS operations would have us believe possible. These events and continued activity will only drive a hidden arms race for other state and non-state actors to mature equivalent weapons to affect industrial infrastructure and ensure parity against possible adversaries.”
In 2017, ICS defender also took enhanced steps to guard against a number of traditional IT malware that have the potential to cripple operational networks. Among these was the release of the EternalBlue vulnerability (MS17-010) and subsequent WannaCry ransomware worm. “The infection of operational networks with this ransomware and operational disruption illustrated the symbiotic relationship between the two networks,” Slowik noted. Later in 2017, NotPetya emerged, weaponizing the EternalBlue exploit and leveraging credential capture and replay to rapidly spread to organizations outside Ukraine.
For Slowik, an intelligence-approach to tackling ICS from threats isn’t enough. “Organizations must understand and consume ICS-specific threat intelligence to monitor for adversary behaviors and tradecraft instead of simply detecting changes, anomalies, or after-the-fact indicators of compromise,” he said.
This proactive approach will require detection-in-depth, such as enhanced monitoring of permeable barriers like the IT-OT network gap. In the event of a breach, companies must be prepared with ICS-specific investigation capabilities and incident response plans. Meanwhile, “Gone are the days of protection via a segmented network—detection is the first component of an assume-breach model—you can only respond to what you can see,” he said. Finally, the value of resiliency is of utmost importance: “Safety systems must be designed and operated with the understanding that they may now be purposefully attacked and undermined,” he said.
A Call to Arms: Hunting and Responding to Cyberattacks
In a report reviewing ICS defense measures and lessons learned from the Fulton, Maryland–firm’s Threat Operations Center (TOC) over 2017, Miller underscored that no single solution can resolve the vast range of troubles faced by ICS operators within their varied work processes.
A more proactive measure is imperative—and he called for a “call to arms,” urging the ICS community to actively hunt for threats. “Recognizing that defenses are fallible and simply waiting for an alert, alarm or notification is simply not enough. It is inherently reliant on a human; adding the cognitive layer to the already existing security controls and security automation,” he said. Threat hunting involves generating a hypothesis, which, in turn, requires a deep understanding of industrial process and facilities.
For Dragos, increased visibility into industrial networks has shed more understanding of infection vectors. (For more, see: “Malware in Modern ICS: Understanding Impact While Avoiding Hype,” in POWER’s May 2017 issue.) One misconception Miller tackles, for example, is that phishing emails and external media are responsible for the significant portion of the infections in industrial networks. Dragos’ TOC engagements showed that the most common vector has to do with external connections, which include external VPN connections to vendors and third-parties as well as partners. That vector is followed by Trojanized software—such as those on exchanged or removable media or downloaded from compromised websites. Then comes internalized connections. Phishing emails as an infection vector falls last. However, numerous incidents were caused by uncommon vectors with a significant impact, Miller noted.
“The recommendation to the ICS security community is to consider the collection bias that can form, assess and address the most common infection vectors including external and internal connections instead of just phishing, and understand the risk of each infection vector posed to the organization instead of fixating only on the most common,” the report says. “It is a best practice to take a few focused goals for this next year such as additional collection, detection, and response efforts on highlighted infection vectors. Focus on making a few significant changes in the right direction instead of trying to address everything by a small amount.”
Miller’s report also provides a list of common shortfalls. Foremost among them is a lack of visibility into the ICS networks. “Without proper visibility, it is more difficult to identify what needs protecting and what controls would return the best investment,” he wrote. “The timeline to triage, scope, and respond to any incident is directly correlated to the visibility available during the time of analysis.”
Miller noted, though, that gaining visibility can be challenging. “The first step and not the last step,” he said, is generating an asset inventory. “What has proven successful and recommended by Dragos is the generation of a Collection Management Framework (CMF),” which is essentially an analysis of what questions need answering and what data sources are available to answer questions. Data sources range from internal sources such as authentication logs to vendor advisories and notifications.
Miller also urged sound cybersecurity incident response procedures, which are typically not tailored to a facility. Dragos has also seen a lack of testing and validation for security controls and procedures, he noted. Otherwise, he cautions, too many organizations establish threat intelligence groups that focus entirely on low-level indicators. “Intelligence reporting should be translated into direct risk and actionable protections for the receiving party. Threat modeling and attack scenarios can facilitate this effort and help organizations identify gaps in protection and detection capabilities.”
—Sonal Patel is a POWER associate editor (@sonalcpatel, @POWERmagazine)