A primitive but unique ransomware variant that emerged in mid-December can forcibly stop a number of processes, including multiple items related to industrial control system (ICS) operations, industrial cybersecurity firm Dragos warned in a detailed report on Feb. 3.
The ransomware known as “EKANS” (or “Snake,” which is “EKANS” spelled backwards) is “relatively straightforward” as a ransomware sample in that it encrypts files and displays a ransom note. However, “all indications at present” show it also contains a “relatively primitive attack mechanism on control system networks,” Dragos said in its report. Of more concern is that “the specificity of processes listed in a static ‘kill list’ shows a level of intentionality previously absent from ransomware targeting the industrial space,” it said.
The security firm said that while EKANS was first identified in a “commercial virus repository” on Dec. 26, 2019, it learned about the malware on Jan. 6, and it alerted impacted parties a week later on Jan. 14. An investigation has since shown that EKANS, an obfuscated ransomware variant written in the Go programming language, is related to MegaCortex, another highly disruptive ransomware that also contains some ICS-specific characteristics.
According to Dragos, though EKANS’s origins are murky, it may not be linked to malicious state-sponsored activity. In its report, the firm refuted media and vendor blog reports that EKANS activity was linked to cyber operations linked to Iran. “Absent any additional context, EKANS instead appears to be a fairly standard ransomware variant, albeit with some additional concerning functionality,” it said. “While there are examples of ransomware-like malware being used as a means to achieve widespread destruction, no evidence exists that EKANS was designed to mimic such functionality.”
Still, the company strongly urged ICS asset owners and operators to review attack surfaces and determine mechanisms to deliver and distribute disruptive malware, such as ransomware, with ICS-specific characteristics. At present, the firm is “not aware” of how EKANS distributes itself within victim networks, it acknowledged. “Primary defense against ransomware such as EKANS relies on preventing it from reaching or spreading through the network in the first place.”
What EKANS Does
Dragos said a binary code analysis conducted on a single known but “relevant” sample shows EKANS uses multiple, custom Go libraries to construct and ensure execution. First, it checks for existence of a mutex value, “EKANS,” on the victim, and if present, it will stop the message. If not, it sets the mutex value and continues encryption using standard encryption library functions. Before it moves to file encryption operations, however, the ransomware forcibly halts processes (or “kills”) that are listed by process name in hard-coded list within the encoded strings of the malware.
“While some of the referenced processes appear to relate to security or management software (e.g., Qihoo 360 Safeguard and Microsoft System Center), the majority of the listed processes concern databases (e.g., Microsoft SQL Server), data backup solutions (e.g., IBM Tivoli), or ICS-related processes,” Dragos said.
Among ICS products, GE’s Proficy data historian, with both client and server processes included, are referenced “numerous” times, Dragos said. Other ICS-specific functionality references includes GE Fanuc licensing server services and Honeywell’s HMIWeb application. Remaining ICS-related items consist of “remote monitoring (e.g., historian-like) or licensing server instance such as FLEXNet and Sentinel HASP license managers and ThingWorx Industrial Connectivity Suite,” the firm added.
Dragos underscored that the malware performs no action other than to forcibly stop referenced processes. That means, it has “no capability to inject commands into or otherwise manipulate ICS-related processes,” it explained. However, if executed on the right system, such as a data historian, it could “induce a loss of view condition within the network,” it warned.
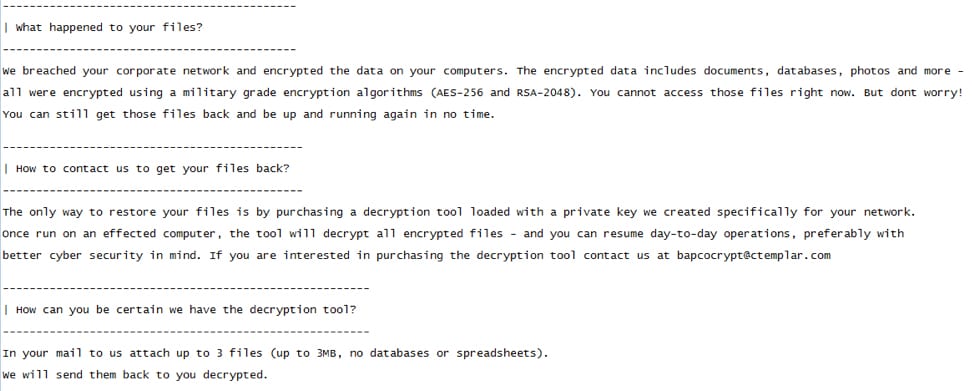
After the EKANS has forcibly stopped processes and executed encryption actions, it drops a ransom note to the root of the system ((typically C:\) and the active user’s desktop. However, unlike more disruptive ransomware such as LockerGoga (which was deployed to force Norsk Hydro’s entire global network offline in March 2019), EKANS does not disrupt user access to the encrypted system, and an affected system does not reboot, shutdown, or close remote access channels, Dragos said.
EKANS processes also have no built-in propagation or spreading mechanism, and it must be launched either interactively or via script to infect a host. “As such, EKANS follows a trend observed in other ransomware families such as Ryuk and MegaCortex among others, where self-propagation is avoided in favor of performing large-scale compromise of an enterprise network,” Dragos said. “Once achieved, ransomware can be seeded and scheduled throughout the network via script, Active Directory compromise, or some other mechanism to achieve simultaneous infection and system disruption.”
EKANS May Be an Evolution of a Formidable Ransomware Variant
Of specific concern to Dragos is that EKANS shows a notable connection with MegaCortex, a ransomware that was thought to infect large corporate networks and workstations in the U.S., Canada, and parts of Europe in May 2019. The firm observed that process kill activity similar to EKANS was observed in a newer, “version 2” variant of MegaCortex in mid-2019, as Accenture reported.
“While the list of processes targeted in EKANS is relatively short and focused (64 total items), the newer version of MegaCortex contains over 1,000 referenced items. The vast majority of the processes listed relate to security solutions or similar tools. However, all of the items referenced in the EKANS ICS list are also present in the MegaCortex list, and no additional items are present in the MegaCortex list with ICS significance,” Dragos said. “Based on this information, it appears EKANS is not unique, or at least not first, in targeting ICS-related processes.”
That means, it warned, with MegaCortex as its presumed “parent”, EKANS is essentially “an obfuscated, hardened ransomware variant based on prior [MegaCortex] activity.”
Why that’s worrisome, the firm explained, is that while ransomware may have previously victimized ICS environments, “prior events all feature IT-focused ransomware that spreads into control system environments by way of enterprise mechanisms. Otherwise, ICS-specific ransomware has mostly included either academic proof of concepts or marketing stunts representing the corpus of activity.”
But EKANS—and apparently some versions of MegaCortex—“shift this narrative as ICS-specific functionality is directly referenced within the malware,” Dragos said. “While some of these processes may reside in typical enterprise IT networks, such as Proficy servers or Microsoft SQL servers, inclusion of HMI software, historian clients, and additional items indicates some minimal, albeit crude, awareness of control system environment processes and functionality,” it said.
Impact on Industrial Environments Unknown—But Experts Urge Preparation
Still, how severely EKANS or MegaCortex could affect industrial environments is unclear, Dragos said. Yet, with what’s known, it’s clear they pose possible threats—and despite the uncertainty, they warrant defensive action to prevent inadvertent loss-of-control situations.
“Targeting historian and data gathering processes at both the client and server level imposes significant costs on an organization and could induce a loss of view condition within the overall plant environment,” said Dragos. “The impacts for licensing server and HMI process termination are less clear, as other processes may still be in play to enable functionality and fallbacks or ‘grace periods’ for licensing servers may enable continued operations for some time absent the license management system.”
In its report, Dragos recommended a long list of ways ICS operators could implement mitigation. It suggests, for example, that for ICS historian operations, organizations can potentially identify a disruptive attack in progress by implementing logic or monitoring on their historian (such as GE Proficy in this case) to identify cases where multiple endpoints cease communication and reporting to the historian at approximately the same time. “While systems may still be offline or compromised, identifying this datapoint early in the investigation will facilitate root cause analysis into the event by identifying potential ICS-specific functionality, such as that displayed in EKANS,” it said.
And as always, the firm urged organizations to generate regular backups of important files and systems, and store them in secure locations that aren’t easily accessible from the regular network. “For ICS operations in particular, backups must include last known-good configuration data, project files, and related items to enable rapid recovery should a disruptive event occur.”
—Sonal Patel is a POWER senior associate editor (@sonalcpatel, @POWERmagazine).