The energy sector has been hit with almost one-third of the cyberattacks against U.S. industrial facilities in recent years. It is among the top issues, along with reliability, environmental regulations, and aging infrastructure, facing power plant operators. New technologies and processes are available to help fight the battle.
The cyberattack on Ukraine’s power grid in December 2016 brought the industry’s vulnerabilities into sharp relief. For decades, the more familiar territory of physical security threats had dominated the conversation. Just before Christmas, the grid attack cut power to 103 cities and towns, leaving nearly 200,000 Ukrainians without power for several hours. The global utility industry felt the ripple effects, and the urgency to address and attempt to prevent cybersecurity threats mounted.
For years, cybersecurity trailed behind reliability, environmental regulations, and aging infrastructure in the list of issues confronting power producers. However, cybersecurity moved firmly into the No. 2 spot in 2016, and recent news of hackers targeting U.S. nuclear power plants proves the threat is very real.
In fact, U.S. industrial control systems were hit by cyberattacks at least 245 times during a 12-month period between 2014 and 2015, according to the U.S. Industrial Control Systems Cyber Emergency Response Team. While every industry is prone to attack, the energy sector led all other industry verticals with almost one-third of the attacks.
Power is a fundamental resource that drives civilization. It is critical to economic and military defense infrastructure; therefore, it’s an obvious target for security threats. For that reason, power generators are actively working to improve their practices and more effectively navigate the cybersecurity landscape. This report looks at today’s challenges, and the way power producers can address cybersecurity concerns and regulations more efficiently and effectively.
Challenges for Bulk Electrical Systems
When it comes to acting on relevant regulatory standards, power producers have to take a holistic approach. The positive news is that, in general, power producers are ahead of the curve when it comes to cybersecurity compared to other industrial companies. Take the recent presidential executive order designed to strengthen the cybersecurity of federal networks and critical infrastructure. It calls for an assessment of cyber readiness and vulnerabilities. The electrical industry is already doing this in order to comply with industry regulations and standards, including North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) standards (see sidebar), the Cybersecurity Act of 2015, and National Institute of Standards and Technology (NIST) standards.
| Tackling NERC CIP Standards
Given the many regulations and standards impacting power producers, it’s hard to process everything at once. The highest priority has to be what must be implemented—namely, the North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) standards. Plan to protect your cyber critical assets: CIP-003, -007, -008, and -009 all offer guidance on securing individual assets within a system. Know what you have and where it is: CIP-002, -005, and -011 are focused on understanding what critical assets exist within a system and what cyber critical assets are essential for the operation of the other assets. Tend to the physical security of your assets: CIP-004, -006, and -010 describe how to create and maintain a physical security plan that complements the cybersecurity measures already in place. |
People rely on power producers to provide economic security, environmental stability, and health infrastructure service in their daily lives. Given the potential for national security threats, it makes sense that these standards are crucial.
The integration of renewable generating assets, propagation of distributed generation, and need for an integrated generation infrastructure has led to multiple progressions in the industry. The first is convergence of information technology (IT) and operational technology (OT) systems for greater collaboration and plant-wide efficiency (Figure 1). The second industry shift is the increase of intelligent devices and smart equipment, which serve as the foundation of a connected power plant (see “The Future Is Now: Connected Power Plants Are Here” in the April 2017 issue).
As power producers work to implement IT/OT convergence and intelligent devices, they must continue to keep cybersecurity threats top-of-mind. The electric power industry, for instance, follows threat mitigation methods that focus on areas such as preparation, prevention, response, and recovery.
It’s no secret that the goal for every facility is to manage risk properly, which might include system upgrades. Still, according to the Edison Electric Institute, there are tens of thousands of power plants in North America, and they cannot be protected from all threats 100% of the time (Figure 2).
In fact, not all producers will be able to upgrade systems and technologies to the same level or at the same pace. For producers building new plants or taking on complete overhauls of an existing facility—such as moving to a more modern infrastructure, control system, or electrical product—this can be an ideal time to investigate and implement cybersecurity protections and processes as part of that larger design and implementation.
Complications
For many established facilities, however, it’s more complicated. They may not have the capital funds available to upgrade problematic legacy systems. Therefore, we’re going to see producers running with their reliable and proven programmable logic controllers in many locations for the remainder of the plant’s lifecycle.
That doesn’t mean those systems can’t get connected or be secured. It just means we’re likely to see a rise in hybrid solutions that allow older facilities to achieve the improved production that comes with greater connectivity and the security required for customer satisfaction and regulatory compliance in a way that’s more immediately financially feasible.
Piecing together the right combination of technology and processes for a hybrid solution presents its own challenges. Plants have access to a plethora of rapidly evolving technologies. Sorting through everything that’s available and articulating how that will translate into the desired functionality and outcomes for an individual facility takes skill.
Most plants don’t have staff with the knowledge and resources required to assess what systems are needed, much less design, deploy, or maintain more secure and connected systems. This issue can be addressed via workforce training and development, or through vendor-provided services and support.
Furthermore, systems can only be successfully designed and deployed if cybersecurity is addressed in an all-inclusive manner.
A Holistic Approach to Cybersecurity
Industrial security must be holistic to be effective. It’s enterprise-wide, starting at the plant level and encompassing every individual and device. It addresses risk from all sides: people, processes, and technologies. And it brings together IT and OT teams, both of which are indispensable in securing network architecture.
There are three key steps to take when employing a holistic approach. First, move forward with a security assessment to understand your risk areas and potential threats. Next, deploy defense-in-depth security to establish multiple fronts of defense. And finally, work with trusted vendors that follow core security principles when designing their products.
Security Assessment.Power producers must cultivate a deep understanding of all risks and vulnerabilities that exist within their organization. A security assessment offers a fresh and unflinching look at site infrastructure nuances, software, networks, control system, policies, procedures, and even employee behaviors. It’s the foundation for a successful security policy.
Key deliverables for any security assessment include:
■ Inventory of authorized and unauthorized devices and software
■ Detailed observation and documentation of system performance
■ Identification of tolerance thresholds and risk/vulnerability indications
■ Prioritization of each vulnerability based on impact and exploitation potential
■ Mitigation techniques required to bring an operation to an acceptable risk state
With an assessment in hand, implementation can begin.
Defense-in-Depth Security. Defense-in-depth (DiD) security is based on the idea that if any one point of protection is defeated, additional layers will subsequently protect the system. Therefore, DiD security establishes multiple layers of protection through a combination of physical, electronic, and procedural safeguards. Just as a bank uses multiple security measures—such as video cameras, a security guard, and a vault—this helps make sure threats encounter more than one line of defense.
A DiD security approach consists of six main components:
■ Policies and procedures play a critical role in shaping workers’ behaviors to follow good security practices and confirming the appropriate security technologies are used.
■ Physical security should limit personnel access to not only areas of a facility but also to entry points on the physical network infrastructure, such as control panels, cabling, and devices.
■ A network security framework should be established to help safeguard your network infrastructure against cyberattacks.
■ Security patch management should be established to track, evaluate, test, and install cybersecurity software patches, because the top means of intruder entry into automation systems is through software vulnerabilities.
■ Security devices should be incorporated at the manufacturing or industrial application level as part of a DiD approach.
■ Device authentication and unauthorized device identification can help ensure only trusted devices are used.
Trusted Vendors. A plant’s automation system is likely a small part of capital assets or costs. However, it can have an outsized impact on helping meet security goals—similar to the impact it has on a plant’s production, quality, and safety goals. Before a vendor is selected for any system that will be connected to a plant’s network, the company should disclose its security policies and practices. For example, Rockwell Automation has defined five core security principles for designing products used in a control system (Table 1).
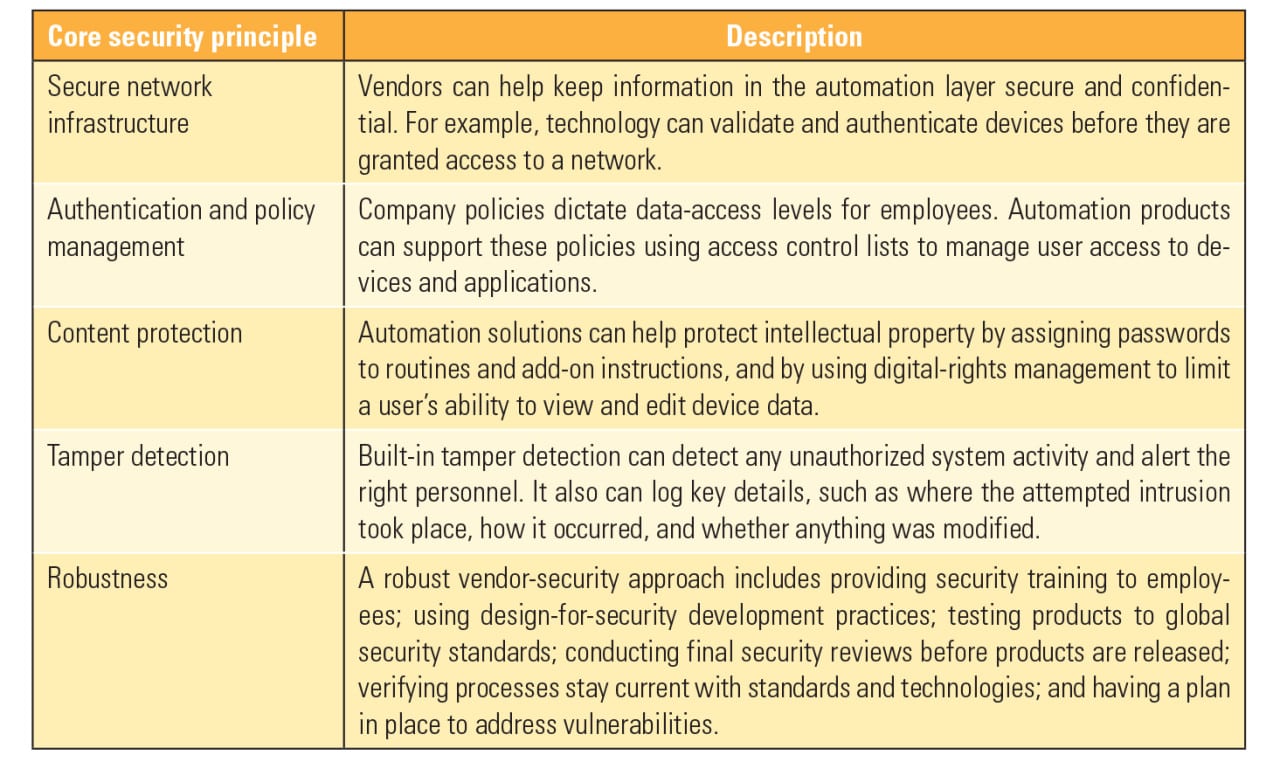 |
| Table 1. Core security principles. Rockwell Automation developed five core principles for designing products used in power plant or other industrial control systems. Source: Rockwell Automation |
Power generators should look for a structured and tailored approach to meet physical and cybersecurity requirements. This can include multiple layers of protection through a combination of physical, electronic, and procedural safeguards. It might include a highly integrated cybersecurity suite that consolidates solutions—such as antivirus, application whitelisting, security information and event management, and compliance—into a unified solution. ■
–Tom McDonnell is the North American Power Generation Industry Leader for Rockwell Automation.