OT
-
Connected Plant
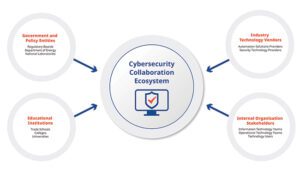
Power in Unity: Strengthening OT Cybersecurity Through Collaboration
Cooperation across teams, technology, and institutions is the key to securing the world’s critical infrastructure. As the global industrial cybersecurity market grows toward a forecasted $41.4 billion in
-
Connected Plant
3 Major Cybersecurity Challenges Facing Critical Infrastructure and OT
Let’s be honest. Operational technology (OT) security issues are expected. Traditional OT systems were designed for specific functional—operational—purposes. Plus, they were designed to last for many decades. The power grid, the water supply, the manufacturing plant floor, these ubiquitous 24/7/365 operations fuel daily activities—and they power as much business as they do hospitals that care […]
-
Press Releases
OPSWAT Enhances its OT Security Solution with Improved Capabilities for Control and Visibility
OPSWAT has enhanced its MetaDefender OT Security solution, empowering organizations with enhanced visibility and control over their Operational Technology (OT) environments. In today’s increasingly complex industrial landscape, industrial and OT teams require complete asset visibility without disrupting OT networks and devices. MetaDefender OT Security addresses these challenges head-on, offering a purpose-built cybersecurity solution tailored to […]
-
Power
Why Utilities Need to Supercharge Their Approach to Cybersecurity
People know a storm can disrupt the electrical grid and cause a wave of complications across the region or country very quickly. But now, for those charged with grid reliability and keeping the lights on
-
Connected Plant
Energy Is the Most-Targeted Sector for Cyberattacks: Here’s What to Do
The energy sector recorded three times as many operational technology (OT) and/or industrial control system (ICS) cybersecurity incidents as the next closest vertical, according to a study conducted by the Cyentia Institute, a research and data science firm, and sponsored by Rockwell Automation, an industrial automation and information provider. “Energy, critical manufacturing, water treatment, and […]
-
Connected Plant
Four Ways to Protect the Energy Sector from Cybersecurity Threats
It’s been two years since the historic Colonial Pipeline ransomware attack shut down one of the largest and most vital oil pipelines in the U.S. While this hasn’t been the nation’s only attack on power infrastructure, it’s the largest publicly disclosed and, at $4.4 million, it was also the most-costly. Since then, we’ve learned that […]
-
Cybersecurity
Modernizing Cybersecurity Practices Within Utilities
The utility industry needs to be prepared to adapt at this time of uncertainty and change, rising prices, and international turmoil. However, it is becoming more challenging to comply with regulations and
-
Connected Plant
Zero Trust: Protecting Critical Infrastructure and Responding to CISA’s ‘Shields Up’
There are no boundaries in cyberspace. That fact has accelerated sharing of threat intelligence across the defenders, but it exponentially raises the threat of cyberattacks. This reality is underscored by the war in Ukraine, “the first major conflict involving large-scale cyber operations,” according to the U.S. Cybersecurity and Infrastructure Agency (CISA). A major concern is […]
-
IIOT
The Growth of Renewables Calls for Scalable Approaches to OT System and Device Integration
Reports from U.S. agencies indicate the use of renewable energy continues to grow. According to the U.S. Energy Information Administration, the U.S. consumed a record amount of renewable energy in 2020. In addition, renewable energy in the U.S. grew for a fifth consecutive year, accounting for 12% of the total U.S. energy consumption. It was […]
-
IIOT
Four Questions You Must Ace to Ensure Sound Cybersecurity in OT Systems
Some cybersecurity experts believe hackers today pose a greater threat than ever to power plants and electric grids. Much of the operational technology (OT) used in power stations and throughout the grid was installed at a time when cybersecurity was more of an afterthought than a focal point in the system design. Furthermore, the pool […]
-
Connected Plant
Implement Cost-Effective, Zero-Trust Remote Operations to Mitigate Cyber Risks and Maintain Operational Resilience
In January 2021, a hacker accessed the digital infrastructure controlling the water supply for Oldsmar, a Florida city of 15,000 people. The bad actor attempted to manipulate the city’s water supply, exploiting a vulnerability in the company’s IT-grade remote access software to alter levels of sodium hydroxide in the water supply, raising its concentration to […]
-
Connected Plant
To Reap the Benefits of Modern Grids, Proactive and Resilient Cybersecurity Is Crucial
Managing a nationwide system of assets providing power generation, transmission, and distribution, which underpin the energy sector, can be a challenging endeavor. Particularly when you take into account the vast array of modern and legacy technologies that may not work in harmony together. For energy professionals, the stakes could not be higher. Prolonged outages as […]
-
Connected Plant
Two Keys for Better Critical Infrastructure Cybersecurity
Two recent incidents have made the cost of not protecting our infrastructure and natural resources abundantly clear. First, there was the widely publicized SolarWinds attack that infected more than a dozen utility companies, and oil and gas manufacturing entities. Then, there was a dangerous incident in Florida, where a hacker gained access to a water […]
-
Connected Plant
5 Cybersecurity Best Practices to Protect Your OT Systems
Over the last several years, cyber actors and online criminal gangs have used cyber warfare to disrupt business and infrastructure across the globe. Today, they are becoming even more aggressive and are using their resources to target Operations Technology (OT) and Industrial Control System (ICS) networks. According to the Canadian government’s Canadian Centre for Cyber […]
-
IIOT
The Energy-Sector Threat: How to Address Cybersecurity Vulnerabilities
Electric-power and gas companies are especially vulnerable to cyberattacks, but a structured approach that applies communication, organizational, and process frameworks can significantly reduce cyber-related risks. In our experience working with utility companies, we have observed three characteristics that make the sector especially vulnerable to contemporary cyberthreats. First is an increased number of threats and actors […]
-
Technology
Digital Transformation: Lessons from a Leader
Is your company’s information technology (IT) department your friend or your enemy? Does it work with you to identify, evaluate, and select the best new digital technology to make your job easier and your
-
Cybersecurity
Using Extreme Visibility to Protect Industrial Control Systems [PODCAST]
What does it mean to have “extreme visibility” in an operational technology (OT) environment? According to Claroty, a New York-based company that offers cybersecurity products for industrial control systems, it’s having the ability to see all assets on a network, knowing what they are, and understanding what functions they perform. The company says the more […]
-
Connected Plant
Cyber Breaches: Is Fear Misplaced?
The power sector’s terror of a debilitating cybersecurity attack is magnified seemingly every day as new vulnerabilities or destructive threat actors are identified. But according to several industrial
-
IIOT Power
DOE Lays Out How Power Sector Could Win the Cybersecurity Battle
Cybersecurity threats are outpacing the energy sector’s “best defenses,” and costs of preventing and responding to cyber incidents are straining company efforts to protect critical infrastructure, the Department of Energy (DOE) warned as it released a comprehensive five-year cybersecurity strategy for the industry. The Multiyear Plan for Energy Sector Cybersecurity, dated March 2018 but which […]
-
IIOT Cyber
Securing Industrial Control Systems: A Holistic Defense-In-Depth Approach
Defense-in-depth is a concept that is already widely deployed by many organizations within their IT infrastructures. However, many organizations do not apply it to their industrial control system (ICS) operations, owing mostly to obscure protocols. But as IT and ICS architectures converge and high-profile cybersecurity incidents mount, a robust, holistic defense-in-depth solution may be […]
-
IIOT Power
DHS, FBI Identify Tactics in Cyberattack Campaign Targeting Industrial Control Systems
The Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) warned in an e-mail on October 20 that an ongoing cyberattack campaign is targeting the nuclear, energy, and other critical infrastructure sectors since at least May 2017—with results ranging from cyber espionage to the ability to disrupt energy systems in the event of […]