Is the sky falling? No, but are there lessons we can learn from Chicken Little? Absolutely. False alarms and fear mongering consume energy we can ill afford to waste, but should some sort of alarm be sounding? Of course.
The challenge is that alarms have the potential to create “white noise.” The constant barrage of headlines may desensitize us to the magnitude of the potential harm. How bad can it be? Perhaps we should look at a few of the major cyber attacks within the past 18 months.
Who would have thought that hackers could have stolen over $1 billion from more than 100 banks in 30 countries in orchestrated attacks? Who would have thought that hackers could have compromised more than 80 million user accounts from one of the nation’s largest banks? Who would have thought that hackers could have accessed sensitive information belonging to 80 million consumers from one of the nation’s largest health insurers? And regarding truly sensitive information, who would have thought that hackers could have accessed sensitive information belonging to all current and former federal employees, including all information about those with security clearances? But does the energy sector face the same harm?
Not If, but When
We regularly read about stolen consumer information, hacked healthcare records, or breached government systems, but what about the critical systems in our energy infrastructure? Stealing consumer or employee information from an electrical utility doesn’t make for a very sexy headline, but what about the impact of compromised industrial control systems in the midst of winter? What about 10,000 commuters jammed for hours due to accidents caused by disabled traffic lights and disrupted emergency services? What about 10,000 elderly consumers with no heat and no ability to call for help? What about healthcare facilities plunged into darkness, forced to rely upon backup generators in the midst of surgeries, unable to access critical medical records on servers knocked offline?
While some perceive it to be the stuff of spy movies, the threat to the energy sector is real. It is only a matter of time before it experiences a major information security incident affecting a large population of consumers. The next big hack in the energy sector is inevitable; the only questions are: Who will be its victims, when will it happen, and how bad will it be?
The danger is that entities within the energy sector not only face the same risks confronted by any business with an online interface, but they also risk intrusion by potentially grid-damaging malware that could result in downed services and devastating humanitarian consequences.
Real… and Underreported
A recent report issued by the Department of Homeland Security (DHS) stated that the Industrial Control Systems–Cyber Emergency Response Team (ICS-CERT) responded to 245 cyber incidents in 2014 (see http://1.usa.gov/1DfWPdd). The energy sector, once again, led all other sectors with the most reported incidents (79). The fact that 32% of the total came from the energy sector tends to indicate that the threat is real, and that the energy sector is a major target. Regarding the number of incidents, it is highly likely that the actual total, and the total directed at the energy sector, was much higher. As the DHS stated, “Many more incidents occur in critical infrastructure that go unreported.”
Of the total, roughly 55% involved advanced persistent threats or sophisticated actors. The scope of the incidents encompassed a wide range of threats and methods for attempting to gain access to both business and control systems infrastructure, including the following:
■ Unauthorized access to and exploitation of Internet-facing industrial control system/supervisory dontrol and data acquisition devices
■ Exploitation of zero-day vulnerabilities in control system devices and software
■ Malware infections within air-gapped control system networks
■ SQL injection via exploitation of web application vulnerabilities
■ Network scanning and probing
■ Lateral movement between network zones
■ Targeted spear-phishing campaigns
■ Strategic website compromises (aka, watering hole attacks)
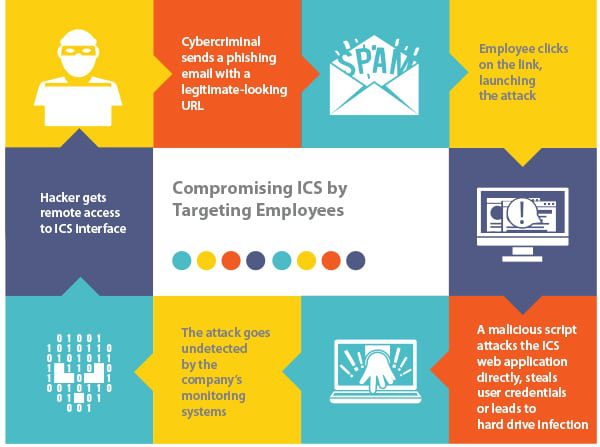
The access vector was unknown for a majority of the incidents. In those instances, the organization was confirmed to be compromised but the forensic evidence did not reveal a method of intrusion because of a lack of detection and monitoring within the compromised networks. Of the known access vectors, however, social engineering combined with technical subterfuge proved to be one of the most successful. Spear phishing, or targeted attacks at individual users, provided access for 42 malicious attacks, or 17% of the total.
ICS-CERT also received 159 reports involving vulnerabilities in control systems components in 2014. The majority of vulnerabilities occurred in the energy sector.
Industrial control systems used to be stand-alone collections of hardware and software, isolated from most external threats. Today, widely integrated software applications and Internet-enabled devices expose these systems to malicious actors who will exploit vulnerabilities, posing significant risks to human health and safety, the environment, and business and government operations. Is the threat real? Absolutely. ■
— Sean B. Hoar is a partner in the privacy and security practice with Davis Wright Tremaine LLP.