Newer types of cyber attacks are harder to identify and protect against than previous types because they can bypass traditional cybersecurity defenses.
It’s certainly no secret that for many years, the power industry has been a top target for hackers around the world. However, whereas in the past, many of these attacks were relatively easy to block using standard security tools like malware detection software, firewalls, and intrusion detection systems, recent advances by state-sponsored hacking teams and criminal groups have made these attacks considerably more sophisticated and harder to prevent.
That’s likely a key reason why 68% of energy companies and others in the critical infrastructure sector admit they’ve been breached by hackers, resulting in either data loss or disruption of operations, according to a 2014 estimate by Unisys and Ponemon Institute.
The reality today is that these attacks are far stealthier than anything the industry has seen before. And the increasingly complex nature of these cyber attacks corresponds directly with the growing level of danger they pose to the power sector.
In 2013 the Department of Homeland Security (DHS) issued an industry-wide alert about the growing threat of cyber sabotage attacks to the power sector after its incident response teams noticed an alarming trend of hackers, possibly from the Middle East, systematically breaching U.S. energy companies in an effort to probe their networks and determine how to take control of key processing systems.
This warning was echoed by National Security Agency Director Admiral Michael Rogers in 2014, when he testified before Congress about the growing threat of cyber-induced power outages and disruptions by foreign governments.
No longer is the theft of trade and technology secrets, or customer data, the top hacking threat for power companies. Instead, their security teams need to be actively preparing for a new wave of stealthy cyber attacks that could be used as a precursor to industrial control system (ICS) “probes” and physically disruptive attacks. While there are a number of different attacks now used by hackers, power companies should focus on these four: cross-site scripting, drive-by downloads, wrappers/packers, and watering holes. All of them can potentially bypass traditional defenses (including both security tools and employee security awareness training) and gain remote access to the network or infect it with dangerous malware.
Understanding the Threat
There are essentially five ways a hacker can gain access to an ICS:
■ Get direct physical access to the ICS (such as via a malicious employee or contractor or an infected hardware device).
■ Find an open Internet-facing port on a control system device using the Shodan search engine or a specialized scanning tool.
■ Steal an employee’s credentials or password to a web application, which is used to access the ICS.
■ Bypass the security configuration of the above-mentioned web application to get access to the control system without a password.
■ Install specialized malware on the energy company’s network that is capable of spreading to the control system.
Out of all of these threats, open Internet-facing ports should be the easiest to prevent simply by auditing the ICS and doing an external search of the network using Shodan. Insider threats are a different breed altogether, and require strict access controls for employees and contractors, as well as background checks, regular supervisory oversight, employee auditing and monitoring, and a diligent password reset policy for terminated personnel.
For the purposes of this article, we’ll be focusing on the last three methods of compromise—all of which involve a more sophisticated remotely based attack without the benefit of an easily accessible port or the help of a malicious insider to facilitate. It is these methods that require more advanced skills in order for the attacker to succeed, and ones that power companies might overlook or under-prioritize, particularly if they think current security controls have already accounted for them.
Breaking Down the Attacks
How does an attacker actually inject malware into the ICS or break into the software used to access or monitor it?
Most of the time it boils down to this: finding the weakest link, which is employees (Figure 1). But wait, some might say, our company puts all of our employees through rigorous security awareness training programs; we also use modern/advanced malware detection systems with anti-phishing controls, strong firewalls, and intrusion detection systems.
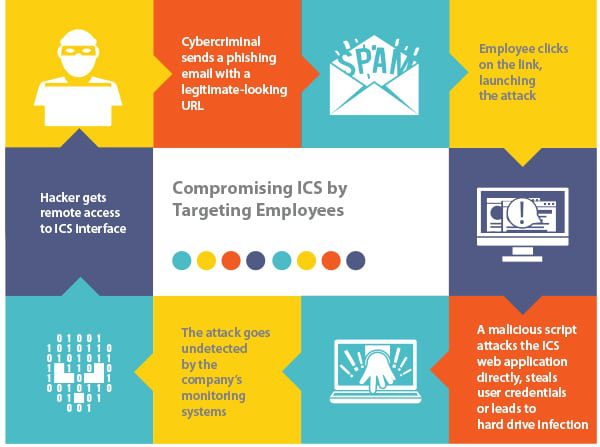 |
| 1. Weakest link: employees. Courtesy: Casaba Security |
That doesn’t matter.
Attacks like cross-site scripting, drive-by downloads, watering holes, and wrappers/packers can often bypass those defenses. To outsmart security tools and employees, they utilize legitimate websites and/or software to conceal themselves and make it much harder to detect them, even if the company is doing a lot of things right. Here’s a brief overview of these attacks.
Cross-Site Scripting (or XSS). In this attack, a hacker takes advantage of weak security in a legitimate web application (which could be running on the company’s internal network as a vendor-provided application, or on a third-party website) to sneak in malicious code that will instantly attack anyone who uses it.
For example, in recent years DHS’ Industrial Control Systems Cyber Emergency Response Team (ICS-CERT) has issued multiple alerts about XSS vulnerabilities in supervisory control and data acquisition/human-machine interface (SCADA/HMI) products. The XSS attack itself may hijack the employee’s ICS software session directly, or it will steal stored credentials or cookies, trick the employee into entering a login and password, which will be sent to the hacker, or cause malicious code to be installed on the employee’s computer hard drive.
This attack is highly dangerous because of its ability to hijack the employee’s access to key systems, like ICS, either through session hijacking, password/credential theft, or computer infection. It’s also difficult for employees to realize they’ve been attacked, because XSS is unlikely to be detected by security programs because it originates from a legitimate application that (without getting too technical) basically tells the security program that it’s not a threat. XSS attacks may also be spread via phishing emails, but they aren’t easy to spot either, because the malicious URL will look completely legitimate, and cybercriminals also use professional “phishing kits,” which look identical to emails sent by real companies and government agencies.
Drive-by Downloads. Similar to the cross-site scripting attack, a drive-by download often takes advantage of a legitimate website in order to dispense malware to anyone who visits it. In some cases, the drive-by occurs when a user clicks on a pop-up window or a third-party ad, but this isn’t required; simply visiting the infected website will immediately activate the malware installation on the employee’s computer.
This attack is particularly dangerous to energy companies because drive-bys are one of the top methods for installing “Trojans” on computer networks. This Trojan could be used to remotely monitor the employee’s machine and steal logins/passwords to ICS software, map the network to find anything connected to the infected PC that it can spread to, create a virtual pipeline into the company’s network that hackers can then use to sneak in all types of malware (such as ICS-targeting malware) without being detected, and remotely control the computer and network as well.
Watering Hole Attack. This attack leverages either cross-site scripting or drive-by downloads but in a far more targeted way. When energy companies are hit by either of these attacks, they will likely be delivered through a watering hole. In fact, in June 2014, Symantec released a report on a massive cyber attack campaign by Russian hackers, which used watering holes and other tactics to infect a wide range of U.S. and global energy companies with Trojans targeting the ICS, which could have been used for sabotage. Earlier that same year, it released another report on targeted attacks on the energy sector, which often used watering holes.
A watering hole is basically a legitimate website (with an unknown security vulnerability, such as XSS) that the attackers have determined people at a particular company or industry frequently visit. Sophisticated attackers, from nation states to organized crime, often look for watering holes as a way to bypass company defenses and beat even security-conscious employees. Due to the risk of watering holes, and other threats, it’s vital for all industrial operators to make sure ICS-connected workstations are completely isolated from the web. These machines should be dedicated to one thing and one thing only: interfacing with the ICS software. They should never be used to check Facebook pages, surf the web, or check email. Give employees a secondary workstation, with a segregated server, to use for accessing websites and other external resources.
Wrappers/Packers. Malware obfuscation plays a key role in most cyber attacks today. Many years ago, hackers figured out that if they could change the “signature” (a string of code in a software program that allows other programs to recognize it, sort of like a fingerprint) of a piece of malware, they could make that malware invisible to antivirus and malware detection programs, even intrusion detection systems. In recent years, criminals have turned this into an art form, and now there are several highly developed methods for making malware undetectable.
One of these is the “wrapper”: this bundles the malware inside a legitimate software program (think PDF, Word doc, computer game, or utility tool), so when the antivirus scans the signature, it thinks it’s a harmless file. Another is a “packer”: This compresses the malware’s signature so much that it’s no longer recognizable, and antivirus will not be able to match it to any red flags. Similarly, a “crypter” will encrypt the malware’s signature so it can’t be matched to known threats. For example, the BlackEnergy malware that has been targeting energy sector ICS environments and drew multiple alerts by ICS-CERT has used both packing and encryption to conceal its true nature.
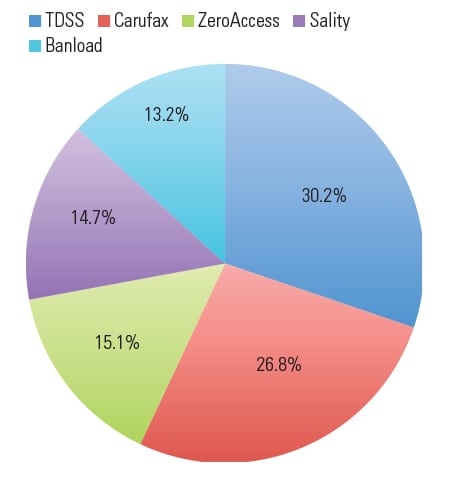
Because the utility sector already has one of the highest incidences of malware per week (221% higher than financial service firms, according to Verizon’s 2015 Data Breach Investigations Report, Figure 2), these advanced techniques pose a significant threat to plant operations.
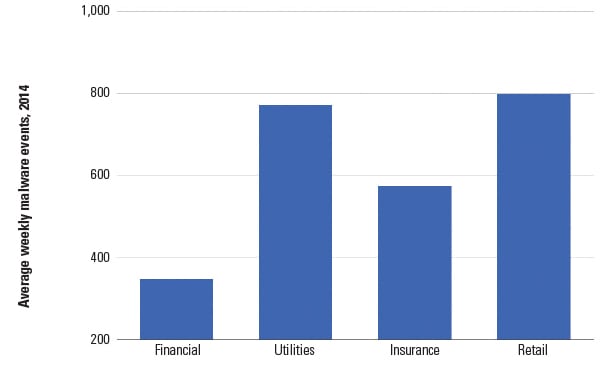 |
| 2. Average weekly malware events by sector, 2014. Source: Verizon 2015 Data Breach Investigations Report |
How to Prevent Stealth Attacks
The only way for the power industry to counter these more advanced attacks targeting ICSs is by taking a defense-in-depth approach, which pays equal attention to prevention and post-breach damage control.
The first step is to establish a strong perimeter defense that can weed out weaker attacks. This of course includes malware detection tools and firewalls, but it also includes email whitelisting for executives and other key employees (like IT administrators); company-wide use of a password manager (but make sure it offers industry standard encryption of any stored credentials); access controls for all employees (one example: don’t allow them to hold administrator-level access on their workstations), contractors, and vendors to the ICS; and routinely auditing the network for any open ports that could potentially be found by search engines, scanning tools or “sniffers.”
However, the power industry should also consider going one step further with its perimeter defense by:
■ Replacing, as often as possible, standard desktops with “thin clients” that don’t allow for local storage (this greatly limits the potential for malware infections).
■ Making sure the malware detection system is integrated with a robust threat intelligence service that will improve its accuracy at spotting new types of malware.
■ Adding script-blocking plugins to employees’ Internet browsers, which will help prevent many “injection” attacks like cross-site scripting.
Next, it’s important to put in place strong security controls “behind the firewall,” for those attacks that are able to get past the first layer of defense. Although intrusion detection systems are less effective today than they were years ago, it’s still worthwhile to have them. However, don’t rely solely on this to detect a breach. Add an extra layer of security by incorporating exfiltration monitoring into the network, which will help uncover previously undetected breaches by spotting unusual network activity and web traffic.
Additionally, consult with a “botnet” intelligence service, which monitors networks of infected machines, to make sure the company doesn’t have any infected devices that are “phoning home” to the attackers (Figure 3). According to BitSight, 52% of utilities have a subpar “botnet grade” of “B” or lower, which means they’re twice as likely to experience a data breach. The energy industry’s botnet grade is worse than those for the financial services sector (26%), retail sector (43%), and healthcare sector (48%). And consider setting up “honeypots” on both the office network and ICS to catch hackers who are probing the network. A honeypot is basically a dummy computer or network node that is there to be attacked in order to gain intel on the attacker. (See “How to Use ‘Honeypots’ to Overcome Cybersecurity Shortcomings” at powermag.com.)
In the third layer of defense, power companies should plan for the worst. Assume the attacker can beat the perimeter security tools and avoid detection by the second layer before executing the attack. The key here is network segmentation and isolation. Try to segment the office network as much as possible so that any malware infection or criminal network access won’t expose the “keys to the kingdom.” That means preventing attackers from being able to move laterally across the entire office network and preventing them from using a foothold on this network to gain access to the ICS.
This is where air-gapping the ICS becomes critical, but a total air-gap is not always feasible. Therefore, it’s essential that any web application or software tool that accesses the industrial network from the office network has been thoroughly tested and patched by the company’s internal security/IT team, as well as by an outside security firm. Both sets of teams should be using multiple methods to find and patch vulnerabilities in these applications, such as “static analysis,” “dynamic testing,” and “black-box testing.”
Finally, every energy company should stress test its networks. The only way to know for sure if a sophisticated hacker can beat a company’s security system is by running “ethical hacking” tests (also known as “white hat hacking” and “black-box testing”), which simulate real-world criminal attacks. Companies need to give these ethical hacking teams a lot of latitude in order to accurately gauge the full extent and severity of the company’s vulnerabilities. Therefore, avoid imposing artificial restrictions on the white hat hacking team’s activity and watch out for company officials who may try to curtail these findings in order to avoid looking bad.
— Jason Glassberg (info@casaba.com) is co-founder of Casaba Security, a cybersecurity and white hat hacking firm that consults for critical infrastructure companies, as well as major technology brands, financials, and government agencies.