Five years ago this August, an extended blackout crippled virtually the entire U.S. Northeast and parts of Canada. According to the Institute of Electrical and Electronics Engineers, it was the largest in North American history, shutting down 62,000 MW of generation capacity serving nearly 35 million homes. The outage cost businesses an estimated $13 billion in productivity and affected users in eight U.S. states and Ontario.
Initial fears that terrorists had caused the blackout were quickly set aside, despite a few claims of responsibility from radical groups. That said, it’s interesting to note that the post-blackout analysis and report by the U.S.-Canada Power System Outage Task Force recommended 46 steps for making another widespread outage less likely. Significantly, 13 of the suggestions called for improving the cyber security of the North American electricity grid.
Doors wide open
The cyber security recommendations shouldn’t have come as a surprise because the experts on the task force know that it’s not hard for any reasonably accomplished hacker to break into interconnected utility control systems. In North America and the rest of the developed world, such control systems are unprotected by commonly accepted cyber security practices, including logging. As a result, those systems are unable to prevent, detect, or produce audit trails of an intentional or unintentional cyber event. It’s more than a little unnerving to consider how much damage can be done to the power grid by a few keystrokes from ill-intentioned hackers sitting at computers anywhere in the world (see figure).

How to thwart an attack. Attacks on utility SCADA networks can occur at any point in the chain of communications. A virtual “electronic security perimeter” should be used to thwart these attacks, regardless of source or target. The host provides control and monitoring of the data network and data logging. The remote service module (RMS) encrypts and compresses network communications with the central host. The remote modem defender (RMD) is the gateway between the network, maintenance land lines, and control points that use analog dial-up lines. Source: Aegis Technologies Inc.
To emphasize the cyber security risks to grids, Joseph M. Weiss, managing director of Applied Control Solutions, testified last October before the U.S. House of Representatives’ Homeland Security Subcommittee on Emerging Threats, Cybersecurity, and Science and Technology. Weiss said that there had already been “more than 90 confirmed control system cyber security incidents. . . . The incidents are international in scope and span several industrial infrastructures including electric power, water, oil/gas, chemical, and manufacturing. With respect to the electric power industry, cyber incidents have occurred in transmission, distribution, and generation including fossil, hydro, and nuclear power plants. Impacts, whether intentional or unintentional, range from trivial to significant environmental discharges, serious equipment damage, and even death.”
Hackers make news
Cyber threats to public and private computer networks are finally getting the attention of major media in the U.S. and around the world. Some control system hackers may only seek to cause mischief, but the damage can be significant, and the impact disruptive and unnerving. For example:
- This March, cnn.com reported on hackers who “operate from a bare apartment on a Chinese island. They are intelligent 20-somethings who seem harmless. But they are hard-core hackers who claim to have gained access to the world’s most sensitive sites, including the Pentagon.”
- Last September, a segment on CNN television depicted a hypothetical and controversial staged penetration of a utility control system by researchers “who launched an experimental cyber attack (and) caused a generator to self-destruct, alarming the federal government and [the electricity] industry about what might happen if such an attack were carried out on a larger scale.”
- This January, the UK-based online IT publication The Register and the British newspaper The Telegraph reported on a Polish teenager who allegedly turned the tram system of the city of Lodz into his own personal train set, triggering chaos and derailing four vehicles in the process. Twelve people were injured in one of the incidents. The 14-year-old modified a TV remote control so it could be used to change track switches. Local police said the youngster trespassed in tram depots to gather the information he needed. The teenager told police that he modified the track settings as a prank.
More than just child’s play
Regulatory bodies now recognize the urgency of neutralizing the threat to the nation’s industrial infrastructure that hackers represent. With control system networks increasingly seen as vulnerable to much more than mischief, public and governmental concerns about the risks of cyber-warfare and cyber-terrorism attacks are growing.
On the U.S. electric power grid, a large number of supervisory control and data acquisition (SCADA) systems are clearly mission-critical. Accordingly, any SCADA-targeted cyber attacks could, in a worst-case scenario, directly or indirectly cause great financial damage through loss or theft of data, actual physical destruction, or even loss of life. In some cases, control systems actually become more vulnerable when they are integrated with TCP/IP networks and applications. And although security solutions and standards have been proposed, in many cases they either include traditional IT security measures that are not compatible with legacy control systems or leave important aspects unaddressed.
To address these vulnerabilities, utilities need to establish an “electronic security perimeter” around their control system networks. Such a perimeter would use advanced data encryption, device and user authentications, defenses against unauthorized dial-up modems, and centralized security monitoring to thwart potential cyber attacks. From a technical standpoint, the perimeter and its supporting framework should have minimal latency and centralized control and management features that meet the power industry’s security needs over both the short and long term.
Identity theft, T&D style
To understand how transmission and distribution (T&D) system vulnerabilities arose, it helps to take a look back at the technology of control systems built before Sept. 11, 2001—this generation’s “day of infamy” that precipitated concern about terrorism on U.S. soil.
Then—as now—in a typical utility system for controlling energy delivery, the system’s master computer and remote terminal units (RTUs) communicate using wireless radio technologies that are easily tapped into by a third party. Even direct T-1 lines, frame relay clouds, fiber optics, and other communications channels can be penetrated by someone with nothing more than moderate technical savvy and desire. For example, a miscreant can initiate a “playback attack” by recording sensitive messages between devices and playing them back later. A more sophisticated attacker could formulate and send new messages designed to override control of remote devices, report incorrect status to the master computer, and/or wreak havoc on system stability.
To this day, most electric utilities’ control systems do not authenticate master and remote devices before allowing them to communicate. Such authentication would allow each device in a network to verify another’s identity, instead of blindly sending out information.
Without authentication, an intruder can engage in what is known as “spoofing”—interjecting message packets that pose as having been sent from a valid device on the network. Because authentication is never done, the receiving device has no way to differentiate malicious packets from authentic packets.
In one possible scenario, a hacker could send to the master computer false status data pretending to be from a remote device. If the false status message is formatted correctly, the master computer will respond as if it were from a real device and disrupt the system.
Another T&D cyber vulnerability is the dial-up connection used by maintenance personnel to remotely diagnose and fix problems with field equipment. Utilities commonly use the technique to avoid the cost and time of sending a technician in a truck to some distant site.
In some remote diagnostic systems, the equipment’s default password either has not been changed or has been set to a nonchanging phrase that many employees and contractors know. One problem with legacy technology environments is that they make it impractical to change the password frequently. Because dial-up diagnostic systems use analog modems, an attacker armed with “war dialer” software and a basic knowledge of control system devices could find it easy to infiltrate a control system through a dial-up connection. And, given that landlines are often not monitored for activity, an attacker could stage a “back door” attack whose source would be very hard or impossible to identify.
Control systems’ final security concern isn’t obvious, but it is very real. In the process of upgrading and expanding their control systems, many utilities and other large infrastructure companies have linked them to supporting IT systems and applications that specialize in billing, accounting, and e-mail. Though this enhanced connectivity and modernization has been a boon for the companies’ productivity, it has exposed their control systems—especially their legacy systems—to the cyber vulnerabilities inherent in IT systems that rely on the Internet. Adding new devices and systems to the interconnected network only creates more possible points of attack.
Serious shortcomings
Based on our experience working with utilities throughout the U.S., Aegis Technologies finds that many are now addressing their control systems’ vulnerability. Unfortunately, many of their chosen solutions are of limited scope and capability.
For example, most “bump-in-the-wire” solutions that encrypt and authenticate a line do not secure dial-up modems. Even when encryption secures a line that has an unprotected modem at its endpoint, the line remains unprotected. In this case, any malicious packets sent through an unsecured modem would simply be encrypted on their way to the master computer.
Furthermore, many solutions lack a centralized management architecture that integrates security logging and monitoring for a common host. In these systems, encryption keys and passwords must be changed at the remote device itself, a costly and time-consuming process for securing substations that are typically far-flung and remote. Without central management, there is no central repository for active security monitoring and reporting. Should a security breach occur, there’s no coordinated way to send alerts to a host operator.
Exemplifying yet another cyber threat, some control system security solutions rely on conventional IT operating systems, such as Linux or Windows, to power remote equipment. Web servers are often also deployed on remote hardware, effectively putting “embedded servers” in the field. Though such configurations may offer some benefits, they are potentially vulnerable to viruses, Trojans, worms, or other cyber nasties that exploit flaws in unpatched versions of the underlying operating system. Many of us know first-hand how difficult it is to rid our home computer of a virus or Trojan. Imagine how much more challenging the task becomes when a virus infects remote equipment far from the control center.
With due respect to the power industry’s embrace of better, more-effective IT systems, most IT-based security solutions fail to acknowledge the needs of control systems. Many of the encryption devices now in use are based on high-speed IT security protocols and/or utilize block encryption algorithms. But these modern technologies require too many resources to operate efficiently on legacy control system networks such as those used by most utilities. The inefficiency leads to unacceptable levels of communications latency in the devices, in turn causing the control system to malfunction.
Finally, existing utility cyber security systems are not likely to be adequate for long-term use. Why? As computing power follows Moore’s Law and continues to double every 18 to 24 months, today’s 64-, 128-, and even 256-bit encryption keys will become easier to hack. Encryption systems must become more robust to cope with the ever-faster technologies that hackers will have at their disposal.
The arms race continues
So, if that’s the scope of the T&D cyber security problem—which has become bigger than anyone cares to acknowledge—what’s the solution?
Step one is for leaders of the nation’s power industry to learn more about the problem and the severity of its consequences. Step two is to begin taking concrete and comprehensive actions to solve it (see table). Humans are usually motivated to address a situation once they recognize that it is indeed a crisis. In this case, utilities must believe that a crippling cyber attack “can happen here” and realize that a security breach might jeopardize both their reputation for excellent service and the revenues and profits that their shareholders demand.
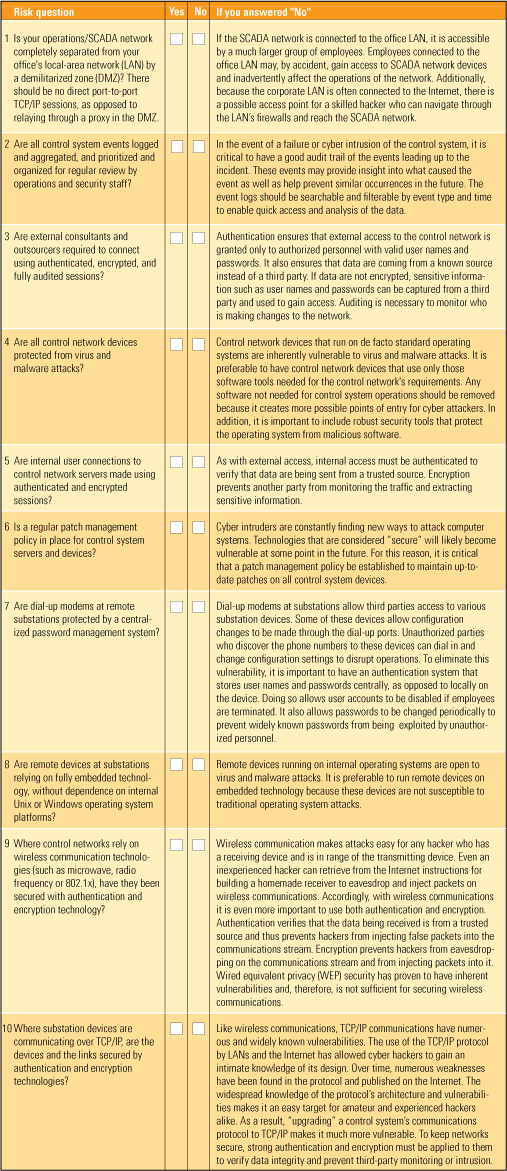
Are your control systems cyber safe? These are the top 10 questions that utility risk managers should be asking about the security of their IT and SCADA systems. Checking “no” for any item indicates that a more in-depth assessment of the utility’s security status is warranted. Source: Aegis Technologies Inc.
When the 9/11 attacks happened seven years ago, one of the reasons cited for not preventing the tragedies was a “failure of imagination.” When it comes to power failures, there’s nothing to imagine, because few of us haven’t had that unsettling experience. This threat is real, and the danger should be clear to the general public. The utilities that step up to the challenge will be the ones that survive and thrive in the years ahead.
—Andrew Bartels (abartels@aegistech.us) is chief technology officer of Phoenix-based Aegis Technologies Inc., a designer, builder, and installer of solutions that improve the longevity, performance, and security of legacy and new control systems.