ICS
-
Connected Plant
Energy Is the Most-Targeted Sector for Cyberattacks: Here’s What to Do
The energy sector recorded three times as many operational technology (OT) and/or industrial control system (ICS) cybersecurity incidents as the next closest vertical, according to a study conducted by the Cyentia Institute, a research and data science firm, and sponsored by Rockwell Automation, an industrial automation and information provider. “Energy, critical manufacturing, water treatment, and […]
-
Cybersecurity
Siemens Energy Investigating Dark Web Ransomware Claim
Siemens Energy and Schneider Electric, two industrial control system (ICS) vendors for critical infrastructure industries, have been reportedly listed as ransomware victims by cybercrime gang CL0P, though any targeted attacks are yet unconfirmed. The ransomware gang, also known as TA505, began exploiting a vulnerability in MOVEit Transfer, an internet-facing automated file transfer web application, starting […]
-
Cybersecurity
Biden Signs National Security Memo Addressing Industrial Control System Cybersecurity
The Biden administration is moving to add more safeguards to the nation’s critical infrastructure by establishing a new voluntary public-private collaboration that will focus wholly on industrial control systems (ICS) cybersecurity. The administration formally launched the “Industrial Control Systems Cybersecurity Initiative” in the “National Security Memorandum on Improving Cybersecurity for Critical Infrastructure Control Systems” signed by […]
-
Connected Plant
Cybersecurity Experts Warn of New ‘Hardened’ ICS-Specific Ransomware Variant
A primitive but unique ransomware variant that emerged in mid-December can forcibly stop a number of processes, including multiple items related to industrial control system (ICS) operations, industrial cybersecurity firm Dragos warned in a detailed report on Feb. 3. The ransomware known as “EKANS” (or “Snake,” which is “EKANS” spelled backwards) is “relatively straightforward” as […]
-
Cybersecurity
Air-Gapped Industrial Control Networks: What You Need to Know
Many networks across a variety of verticals including government, military, financial services, power plants, and industrial manufacturing have been so-called “air-gapped.” This means they are physically and logically isolated from other networks where communication between these networks is not physically or logically possible. This can be a good thing or bad thing depending on your […]
-
Cybersecurity
Using Extreme Visibility to Protect Industrial Control Systems [PODCAST]
What does it mean to have “extreme visibility” in an operational technology (OT) environment? According to Claroty, a New York-based company that offers cybersecurity products for industrial control systems, it’s having the ability to see all assets on a network, knowing what they are, and understanding what functions they perform. The company says the more […]
-
News
TRITON/TRISIS Cyberattacker Has a New Target: Power Sector
XENOTIME, a cyberthreat activity group thought responsible for TRISIS/TRITON malware attacks on safety instrumented systems (SIS) at an oil and gas Middle Eastern facility in 2017, has been probing power company networks in the U.S. and elsewhere, new intelligence from industrial control systems (ICS) security firm Dragos shows. “In February 2019, Dragos identified a change in […]
-
Cybersecurity
Modifying Behavior to Protect Systems in a Malicious Threat Landscape
The malicious threat landscape for industrial control systems (ICSs) is constantly evolving and getting more sophisticated, thereby raising the need to have visibility, implement protective controls, and perform continuous monitoring. As a result, it is important to take a look at the attack vectors of some malware/malicious events—such as Triton—that have occurred over the last […]
-
Cybersecurity
New Cyberattack by Group Behind TRITON/TRISIS Reported
Cybersecurity firm FireEye has uncovered and is responding to a new intrusion at an unnamed critical infrastructure facility that it suggests in an April 10 blog post was perpetrated by the group behind the TRITON attack, which prompted a process shutdown at a Middle Eastern facility in 2017. But while details of the new attack are sparse, […]
-
Connected Plant
Hackers May Already be in Your Infrastructure—Now What?
Cyber-attacks on industrial control systems (ICSs) are no longer a hypothetical. As pieced together by the Wall Street Journal, in 2017, Russian hackers attacked a small construction company, exploiting the organization’s connections with utilities and government agencies. Through an integrator, the hackers accessed computer-network credentials, giving them the ability to get into computer systems that […]
-
Connected Plant
A Grim Gap: Cybersecurity of Level 1 Field Devices
Industrial control system cybersecurity is today largely focused on securing networks, and efforts largely ignore process control equipment that is crucial for plant safety and reliability, leaving it woefully
-
IIOT
CyberX Receives U.S. Technology Patent for ICS Threat Monitoring Analytics
CyberX Technology Recognized as Innovative for Advanced Behavioral Analytics and Machine Learning Algorithms to Accurately Detect Industrial Cyber Risk BOSTON, January 9, 2018 – CyberX, the IIoT and industrial control system (ICS) security company, today announced that it was awarded a patent (U.S. Patent 10,015,188) by the U.S. Patent and Trademark Office for its innovative, […]
-
Cybersecurity
Three Things ICS Security Pros Can Do to Maximize Uptime
Before industrial control systems (ICSs) were network-connected, operators had little to worry about in the way of cyber threats. But as industrial environments, such as energy utilities, become more connected, they’re exposed to vulnerabilities and attacks. ICSs are used in large amounts of critical infrastructure, including the electrical grid, transportation systems, and wastewater plants. How […]
-
Connected Plant
Cyber Breaches: Is Fear Misplaced?
The power sector’s terror of a debilitating cybersecurity attack is magnified seemingly every day as new vulnerabilities or destructive threat actors are identified. But according to several industrial
-
IIOT Aerospace
Bill Codifying Federal Role in ICS Cybersecurity Clears House
A bill codifying the Department of Homeland Security’s (DHS’s) role in addressing industrial control systems (ICS) cybersecurity has cleared the U.S. House of Representatives. While H.R. 5733, “DHS Industrial Control Systems Capabilities Enhancement Act,” contains no mandates for the private sector, it directs the DHS’s National Cybersecurity and Communications Integration Center (NCCIC) to develop and maintain […]
-
IIOT Cyber
Securing Industrial Control Systems: A Holistic Defense-In-Depth Approach
Defense-in-depth is a concept that is already widely deployed by many organizations within their IT infrastructures. However, many organizations do not apply it to their industrial control system (ICS) operations, owing mostly to obscure protocols. But as IT and ICS architectures converge and high-profile cybersecurity incidents mount, a robust, holistic defense-in-depth solution may be […]
-
Instrumentation & Controls
Russian Cyber Threat Actors Have Gained Access to Power Plant ICS Systems
Russian government cyber threat actors have infiltrated workstations and servers of corporate networks containing data output from industrial control systems (ICS) or supervisory control and data acquisition (SCADA) systems associated with an unnamed number of power plants, the Department of Homeland Security (DHS) has warned. The dire warning issued by the agency’s U.S. Computer Emergency […]
-
IIOT Power
DHS, FBI Identify Tactics in Cyberattack Campaign Targeting Industrial Control Systems
The Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) warned in an e-mail on October 20 that an ongoing cyberattack campaign is targeting the nuclear, energy, and other critical infrastructure sectors since at least May 2017—with results ranging from cyber espionage to the ability to disrupt energy systems in the event of […]
-
Connected Plant
Malware in Modern ICS: Understanding Impact While Avoiding Hype
Understanding the threat posed to industrial control systems (ICSs) by malware is difficult. It requires knowledge of proper ICS functionality in order to identify illegitimate software. One industrial
-
Press Releases
Kaspersky Lab Discovers Vulnerable Industrial Control Systems Likely Belonging to Large Organizations
The Majority of ICS Components Connected to the Internet Are Located in the United States and Europe WOBURN, Mass.–(BUSINESS WIRE)–Kaspersky Lab released its report on the Industrial Control Systems (ICS) threat landscape, which revealed that large organizations likely have ICS components connected to the internet that could allow cybercriminals to attack critical infrastructure systems. The […]
-
IIOT Power
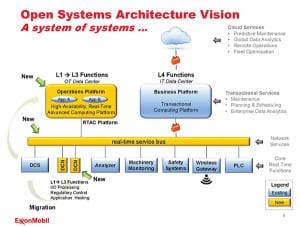
Are Open System Controls Coming to Power Plants?
In the information technology world, open-source platforms and software, as an alternative to proprietary ones, have long been commonly accepted. In process controls, not so much. That could be changing if some large customers have their way. For decades, the norm with industrial plant distributed control systems (DCS) has been that you buy a proprietary […]
-
Instrumentation & Controls
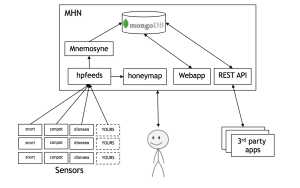
How to Use “Honeypots” to Overcome Cybersecurity Shortcomings
Cybersecurity threats facing the power industry have escalated dramatically in the past few years, as state-sponsored, organized crime, and hacktivist groups all seek to infiltrate U.S. energy infrastructure for cyber-espionage and sabotage purposes. A recent example of the severity of this threat can be seen in operation “Energetic Bear”—a Russian campaign to infect U.S. and […]
-
Cybersecurity
Introduction to NERC CIP Version 5
The North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) standards Version 5 represents the first major change in requirements and approach since its predecessor, Urgent
-
Cybersecurity
Identifying CIP Version 5 Assets in Generation
Generators of electric power face a big effort to comply with the upcoming North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) Version 5 (V5) cybersecurity standards
-
Instrumentation & Controls
Quantum Cryptography Promises Un-Hackable Industrial Communications
Cybersecurity awareness and best practices are increasingly central to the power generation, transmission, and distribution industry. Industrial cybersecurity concerns, recently heightened by awareness of how
-
Instrumentation & Controls
What You Need to Know (and Don’t) About the AURORA Vulnerability
Perhaps because the public has been more obsessed in recent years by cybersecurity breaches involving everything from social media accounts to classified military secrets, the amount of attention given to the
-
Instrumentation & Controls
New ISA Cybersecurity Standard Published for Industrial Control Systems
A recently published standard has been adopted globally to address risks arising from the use of business information technology (IT) cybersecurity solutions to address industrial automation and control systems (IACS) cybersecurity in complex and dangerous manufacturing and processing applications. The ISA-62443 series of standards, being developed by the ISA99 committee of the International Society of […]