Even more than technology and processes, power and utilities leaders must focus on that most timeless of resources—people—to be successful against a landscape of ever-evolving cybersecurity threats. Users, leadership, boards of directors, technical staff, and even marketers are key components of a layered defense.
When positioned poorly, information security offices can become sources of “no” rather than “know”—obstructers rather than key business enablers and partners. In such an environment, chief information security officers (CISOs) or other cybersecurity leaders can be excluded from critical decision-making or governing bodies within the organization when they need to be trusted advisors with their peers, superiors, and the board. Organizations that have built relationships and trust among many stakeholders, and have included them in the development, implementation, and exercising of policy and incident response plans, are far more likely to reduce the impact and enduring consequences of sophisticated hacks like SolarWinds or Pipedream.
COMMENTARY
Understanding where there are gaps and leveraging other internal or external organizations to fill them is building partner capacity. Through regular collaboration, leaders lay the groundwork for empowering resources who are then ready to be further mobilized when needed, filling gaps and avoiding unnecessary expenditure of resources. Digital forensics is a great example of a high-demand, low-density resource that can be very expensive to grow and maintain. Therefore, investing in an enterprise license that provides this on demand, or entering into a memorandum of agreement with a subsidiary that has an organic capability, provides partner capacity that can be leveraged when needed.
Here are eight human-centered actions that organizations can focus on for greater partner capacity from top to bottom in an organization—and ultimately enhanced security.
Advocate for CISOs to Have a Seat at the Table within the C-Suite
Cybersecurity is core to the mission of the enterprise risk management function. CISOs are typically responsible for managing the cybersecurity program and working with other risk practitioners to understand and manage risks across the organization. Depending on the organization, the CISO’s reporting line can vary from the CIO to the CEO to the board of directors. Regardless of whom they report to, they must be trusted as a mission-enabler and have the authority to act in response to an emergency, manage the cybersecurity budget, and write/enforce policy.
The credibility embedded in this line of reporting is vital for communicating risk across functional areas, and how an organization can collectively mitigate risk to mission. It’s essential that the CEO understands that the CISO is a core part of the risk management team who will enable timely, risk-informed decisions during a crisis. Just as important is identifying those stakeholders and exercising risk management crisis response on a regular basis so it becomes second nature.
Connect the Board of Directors with a Trusted Cyber Advisor
Although cybersecurity is top of mind for board members in power and utilities (P&U) organizations, and they should be used to seeing key cybersecurity performance indicators, they are typically not technologists. CISOs should craft their communications to the board in a way that resonates with board members and communicates risk to the business. If deeper technical discussions are required to make a point or reach an investment decision, then it is helpful to have an advisor on the board who can engage in deeper technical discussions with the CISO.
Don’t waste an opportunity to engage with the board by showing up empty-handed. Come up with a format that updates the board on changes in the risk posture or threat environment, and that presents decisions about resources or anything else needed from the board, any actions or changes in policy or processes, and anything exposing the organization to unnecessary risk. Cyber intelligence and geopolitical news that could impact the business always gets people’s attention because it resonates with most business leaders. Geopolitics and cybersecurity are also increasingly intertwined, so if the CISO can build a story around these two topics it is usually well received by the board.
Get Out of the Office and Into the Business
Day-to-day cyber work will likely not help anyone understand the business to be enabled and the data to be protected. All stakeholders can be siloed, to some degree. Who owns the missions and functions? What do they expect, and how can those expectations be met? Without dialogue, leaders can’t build trust and manage the necessary risks through reporting lines. It’s important for CISOs to understand the missions and priorities of functional groups to be able to build a dialogue around cybersecurity.
Many roles need to be part of that dialogue. For instance, marketing and communications is an important department, as public relations is a vital capability in a crisis. CISOs need to put on a hard hat and go see the plant managers, especially as information technology (IT) and operational technology (OT) continue to converge. Their goal is to be 100% up to generate power, and anything new that is put into operations presents a way to short-circuit that metric. Discuss how IT and OT cyber risk management programs can be designed to overlap as much as possible (for example, in zero-trust and multifactor authentication), which helps with talent and transferability of knowledge. Help them understand how security is an enabler of reliable operations—and that a security event, even a small one, creates disruption.
Build a Core Team Focused on Incident Response
Put together a group of trusted incident response and cybersecurity leaders from across functions, and get them to meet quarterly, perhaps hosting on a revolving basis. Each person gains a forum to talk about their hard problems. Dialogue can lead to practical, achievable solutions—in essence, building partner capacity in action.
The collaboration and trust engendered in these discussions can be just as valuable as the solutions. In a crisis, getting the team back together promptly to pool resources and execute a plan of action becomes second nature.
Look Beyond Core Technical Capabilities When Recruiting
Talent is on everyone’s minds these days: how to attract and retain core groups of people whose skills are in demand in every sector, and who may not necessarily be attracted to the P&U sector. The good news is that more cybersecurity vendors are building artificial intelligence (AI) into their products, particularly in alert monitoring and response, to cut through the noise and make technology easier to use. Understand that most of us learn on the job, and endeavor to create an environment where continuous learning can happen for those with ambition.
In today’s environment, don’t overlook skills that are transformative but not as technical—for instance, comfort with new ways of working, and the ability to be inspirational and drive agility. Look for hungry, curious people, often early in their careers, who crave the opportunity to get their hands on something new. Have lunches with them and give them attention and education to grow their own skills and position themselves in the organization, perhaps by testing new cyber products on the market. The ability to fail fast, learn, and innovate doesn’t necessarily overlap with a certain academic degree or training program—it’s a mindset.
Shift Mindsets by Broadening the Concept of Safety
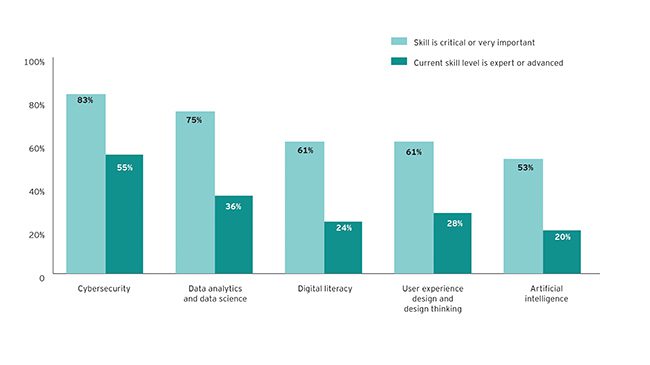
In a recent EY survey, P&U executives said that cybersecurity was the most important technical skill their organizations needed, with 83% ranking it as critical or very important (Figure 1). Yet, just 55% told us that their current capabilities in this area could be described as expert or advanced. Here, partner capacity is crucial for mobilizing the entire organization to elevate a culture of cybersecurity—and P&U companies have been in this position before.
 |
|
1. Importance of technical skills versus current skill level. Source: Power & Utilities Digital Transformation and the Workforce Survey, Ernst & Young LLP, 2021. |
About 20 years ago, the industry rallied around physical safety as core to its mission of delivering safe, reliable electricity. It has become ingrained in the culture, even among those working in office buildings, with safety moments at the beginning of corporate meetings, because their decisions can negatively impact those in the field. Today, we need “cyber moments,” mimicking the same safety hygiene for the virtual world and not just the physical: many groups of people working toward that same mission, with an awareness of the landscape of risks. Embed safe expectations in the cyber realm into performance expectations, driving home that everyone has a role in cybersecurity—not just IT—and the human element of risk. All employees should be equipped with the know-how to protect themselves, their employer, and their nation.
Cross-Pollinate Knowledge with Creative Flair
When leaders have relationships with others in the organization, and there is a mutual understanding around improving the company culture, it becomes easier to get people to attend training and awareness events. Focus just as much on rewarding good behaviors as punishing mistakes, if not more. Look out for those who can collaborate with legal, human resources, marketing, and other functions who can help get the right message to the right person at the right time. Unfortunately, the ability to rally the troops can be rare in the cyber world.
Rotations are also useful. Just as CISOs should reach out to other functions, so should other functions reach out to the CISO and to each other. Consider how P&U companies are losing control system operators, taking their knowledge into retirement with few university programs educating the next generation. Rotating an interested resource into the operations center could open their eyes for new areas to cultivate skills in, while also letting them know the types of problems others are dealing with.
Manage the Personalities
When building partner capacity, personalities in the room can become barriers. Resolving the potential complications is more of an art than a science. But it begins with understanding those organizations to build partnerships with and having multiple people as contacts within them.
Perhaps the CISO’s predecessor had put a certain leader on the defensive, or the function has been historically neglected in decision-making. The only way to repair these relationships is to deliver on promises. Leaders shouldn’t make promises they cannot deliver on—instead, as a first step, they must figure out where they can add value and come up with small, achievable solutions to execute on quickly.
Looked at from a different angle, these challenges can be seen as opportunities for greater understanding—and more partner capacity—so that organizations have hundreds or thousands of cybersecurity advocates from top to bottom, not just in one function. In today’s evolving landscape of threats targeting P&U companies in particular, people can be either the weakest individual link or the strongest collective defense.
—Greg Sisson and Chris Roche are managing directors, and Hetal Patel is a principal, all with Ernst & Young LLP. The opinions in this article are those of the authors.











