Features
-
Legal & Regulatory
The Voters Were Right: Colorado and Minnesota’s Paths to Clean Energy
Voters in Colorado and stakeholders in Minnesota forced through unique managed generation transformation plans that paved the way for aggressive state renewable and clean energy standards—inadvertently pushing their utilities out in front of proposed and now actual federal policies. As the power industry struggles with rising costs of adaptation, many beleaguered executives are anxiously focusing […]
-
Nuclear
Riding Off into the Sunset: Nuclear Decontamination and Decommissioning Update
The International Energy Agency predicts that nearly 200 reactors will be decommissioned during the next 25 years. Industry best practices and new technology can help make the process go more smoothly. It may not come as a surprise, but the average age of operating reactors in the U.S. is greater than 35 years. There hasn’t […]
-
Renewables
The Clean and Dirty of Landfill Gas Power
Despite its apparent environmental benefits and strong government backing, generating power from landfill gas hasn’t gained traction for a variety of reasons in the U.S. Will the Clean Power Plan bolster this “dirty” renewable power source? For the U.S. Environmental Protection Agency (EPA), the only clean thing about landfills—those engineered dumps that entomb America’s infinite […]
-
Business
Public Power “Big Dog” TVA Takes Fresh Approach to Resource Planning
At the Tennessee Valley Authority (TVA), generation transitions are nothing new. The nation’s largest public power system—with 34 GW of generating capacity, supplying retail distributors with nine million
-
Coal
Xcel Energy’s Harrington Generating Station Earns Powder River Basin Coal Users’ Group Award
Harrington Generating Station, located near Amarillo, Texas, began burning Powder River Basin (PRB) coal when its units first entered service, beginning in 1976. A unique feature of the plant is that TUCO Inc. buys and delivers the coal and Savage Services owns and operates the plant’s coal-handling facility. Incomparable housekeeping and exceptional safety performance evidence […]
-
Nuclear
California Drought and Power Potential
California’s grid gurus say they can make it through this summer, but the future may pose real problems for a hydro-heavy regional system. As the grip of California’s four-year drought tightens, will the long-running event crimp electricity generation in the state? So far, according to the California Independent System Operator (CAISO), which dispatches much of […]
Tagged in: -
O&M
CO2 Blasting Restores HRSG Performance
Steam production is strongly influenced by the cleanliness of the gas-side heat transfer surface in a heat recovery steam generator (HRSG). However, when deposits begin to impede heat transfer or increase gas-side pressure drop, it is time for a cleaning. CO2 pellet blasting is a cost-effective and environmentally benign cleaning method available to power plant […]
-
Business
Duke Energy Generation: Wholesale Retreat
Duke Energy, the largest electric utility in the U.S. in terms of market value, is transitioning its generating fleet away from volatile and sometimes unprofitable wholesale markets and toward the traditional, regulated, cost-of-service model that prevails in much of the Carolinas and Florida service territories where Duke dominates. Late last March, the Federal Energy Regulatory […]
Tagged in: -
Legal & Regulatory
Executives Say Power Sector Faces Fundamental Changes
Four industry executives sometimes agreed, and sometimes disagreed, about the great unknowns concerning the Environmental Protection Agency’s Clean Power Plan during the Executive Roundtable at this year’s ELECTRIC POWER Conference & Exhibition. What problems will the Obama administration’s upcoming Clean Power Plan (CPP) deliver to the executives who manage the companies that make the power? […]
-
Cybersecurity
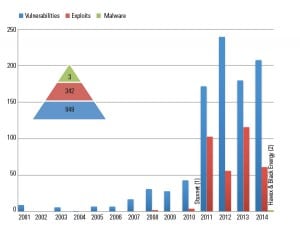
Has Your ICS Been Breached? Are You Sure? How Do You Know?
Since 2010, the year Stuxnet was discovered, there has been an increase in industrial control system (ICS) vulnerability research and reported vulnerabilities, exploits, and ICS-specific malware (Figure 1)