cyberattack
-
Commentary
Cyberattack Vulnerabilities of Modern Power Systems
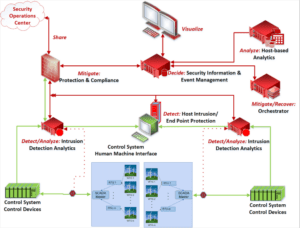
Supervisory control and data acquisition (SCADA) is crucial to contemporary power systems and is widely used in industry and defense. SCADA are computer-based systems that are used to centrally control, monitor, and analyze activities in industries and power systems. This entails real-time communication over a communication network between a central entity and the local controllers […]
-
Commentary
Stronger Cybersecurity Key to Utility Infrastructure
Cybersecurity risks can occur daily, taking multiple forms. While there are personal measures that the general population can do to eliminate some of these risks, power utility companies must take a more aggressive approach to keep the communities they serve safe and their security unquestioned. COMMENTARY Should a power utility company face a cyberattack, it […]
-
IIOT
Digitalisation and Cyber Resilience: Why the Energy and Utilities Sector Is a Top Target for Cybercrime
The energy and utilities sector is not just the lifeblood of the world’s economy, but fundamental to society’s existence as a whole. Yet, recent events have highlighted just how volatile and unpredictable it can be. Output is influenced by everything from weather patterns to war, and no business, consumer, or household is immune from the […]
-
Connected Plant
Security of Cyber-Physical Systems
“Cyber-physical systems” are the next generation of closely integrated physical and cyber systems. Several critical systems such as the power grid, autonomous transportation systems, and process control systems are examples of cyber-physical systems. They are liable to be attacked by malicious agents who can compromise the sensor measurements being used to control them. Indeed, there […]
-
IIOT
Quantum Technology: Applications in Cybersecurity for Power Utilities
With the advent and implementation of smart grid infrastructure across power utilities, there has been a paradigm shift in the efficiencies of the grid. The use of digital communication technology has led to high-speed communication enablement across various components as well as better data analysis and real-time control. This has proven to be advantageous not […]
-
IIOT
Four Questions You Must Ace to Ensure Sound Cybersecurity in OT Systems
Some cybersecurity experts believe hackers today pose a greater threat than ever to power plants and electric grids. Much of the operational technology (OT) used in power stations and throughout the grid was installed at a time when cybersecurity was more of an afterthought than a focal point in the system design. Furthermore, the pool […]
-
Connected Plant
Distributed Renewables’ Cyber Resilience
The benefits of renewable energy continue to grow, with wind generation supplying 9.2% of generation in the U.S. and up to 22.6% in other western countries like Germany. Solar is at 2.8% in the U.S. (for utility-scale installations) and near 10% in Germany. Through diversification and greater distribution system integration, the application of renewable energy […]
-
IIOT
Three Things Utility Companies Need to Do to Prevent the Next Cyberattack
For the better part of the past decade, utility companies have been more concerned with the potential for outages than cyberattacks, but this has changed over the past several months. The Colonial Pipeline ransomware attack and the remote cyberattack on a Florida water treatment plant put cybersecurity top-of-mind and made it clear hackers can do […]
-
IIOT Power
Monitor, Teach, Protect: Three Priorities for Insider Threat Prevention in the Energy Sector
In December 2020, the U.S. Department of Energy announced a new subcommittee focused on the nation’s electric grid. The Grid Resilience for National Security subcommittee was a response to increasing threats to the country’s expansive electric grid that reliably delivers electricity to power the digital age. Today, those threats are even more relevant than ever […]
-
Cybersecurity
Cybersecurity Is More Important Than Ever Due to COVID-19
The COVID-19 outbreak has forced many companies to change the way they conduct operations. Leaders have had to divide employees into essential and non-essential categories. Essential employees must report to
-
Cybersecurity
ICS ATT&CK: Designed to Help Protect from Cyber Attacks
Earlier this year, MITRE—a not-for-profit organization that works in the public interest across federal, state, and local governments, as well as with industry and academia—officially released the long-awaited industrial control systems (ICS) version of its popular ATT&CK knowledge base. ICS ATT&CK is the group’s response to the unique attack surface that industrial networks are trying […]
-
News
TRITON/TRISIS Cyberattacker Has a New Target: Power Sector
XENOTIME, a cyberthreat activity group thought responsible for TRISIS/TRITON malware attacks on safety instrumented systems (SIS) at an oil and gas Middle Eastern facility in 2017, has been probing power company networks in the U.S. and elsewhere, new intelligence from industrial control systems (ICS) security firm Dragos shows. “In February 2019, Dragos identified a change in […]
-
Cybersecurity
New Cyberattack by Group Behind TRITON/TRISIS Reported
Cybersecurity firm FireEye has uncovered and is responding to a new intrusion at an unnamed critical infrastructure facility that it suggests in an April 10 blog post was perpetrated by the group behind the TRITON attack, which prompted a process shutdown at a Middle Eastern facility in 2017. But while details of the new attack are sparse, […]
-
IIOT Power
DHS, FBI Identify Tactics in Cyberattack Campaign Targeting Industrial Control Systems
The Department of Homeland Security (DHS) and Federal Bureau of Investigation (FBI) warned in an e-mail on October 20 that an ongoing cyberattack campaign is targeting the nuclear, energy, and other critical infrastructure sectors since at least May 2017—with results ranging from cyber espionage to the ability to disrupt energy systems in the event of […]
-
Nuclear
Russian Hackers Targeting U.S. Nuclear Plants: Reports
U.S. officials said Russian government hackers have broken into systems at U.S. nuclear power plants and also have made cyber intrusions into the business systems of other energy companies, according to several reports over the past week. Cybersecurity experts say the threats against U.S. facilities are real and likely to continue, as power plant operators […]
-
Connected Plant
Cybersecurity: Keeping Current on a Moving Target
What it means to have a secure energy generating facility has changed in recent years as the threat of cyberattacks grows. As the nation’s energy sector becomes increasingly interconnected, it is more
-
Cybersecurity
Iranian Cyberattack Infiltrated Control System of New York Dam
Hackers believed to be connected to Iran infiltrated the control system of a small dam outside New York City in 2013, according to a report in the Wall Street Journal. The Bowman Avenue Dam in Rye Brook, about 20 miles northeast of the city, is small and used only for flood control. While the hackers […]
-
Nuclear
Korea Hydro and Nuclear Power Co. Hacked
Computer systems at Korea Hydro and Nuclear Power Co. (KHNP)—the operator of South Korea’s 23 commercial nuclear reactors—were hacked and information divulged via blog posts and posts on Twitter, according to the company. The first leaks on Dec. 15 were of personal information obtained from some of the 10,799 employees of the company, but later […]
-
Cybersecurity
Russian Hackers Targeting Energy Sector, Says Report
A group of hackers apparently based in Moscow has been conducting an “ongoing cyberespionage campaign” against energy sector companies in the U.S. and Western Europe, according to a report released June 30 by computer security firm Symantec. The targets included “energy grid operators, major electricity generation firms, petroleum pipeline operators, and energy industry industrial equipment […]