Even before the Stuxnet malware program made international headlines in 2010, cybersecurity was an important issue for utility companies. In the aftermath of one of the largest attacks on supervisory control and data acquisition (SCADA) systems, the front against cyberattacks came together in a new and stronger form. How can we protect today’s energy systems from attacks?
In an artificially illuminated space, all their attention is focused on the monitors of their notebooks. These two men are invaders. They’re creative and they’re equipped with computers, algorithms, malware programs, and all kinds of IT expertise. Their goal is to hack into the control and protection (C&P) system of a high-voltage direct-current (HVDC) transmission system. They have the tremendous advantage of already being inside the control center surrounded by more than 30 control panels.
Fortunately, their presence here isn’t cause for alarm. Unlike cyberattacks that come from the outside, this attack is being expressly solicited. It’s what’s called a penetration test, or pen test for short, and it’s an important part of the higher-level function performance test (FPT) performed on HVDC transmission systems.
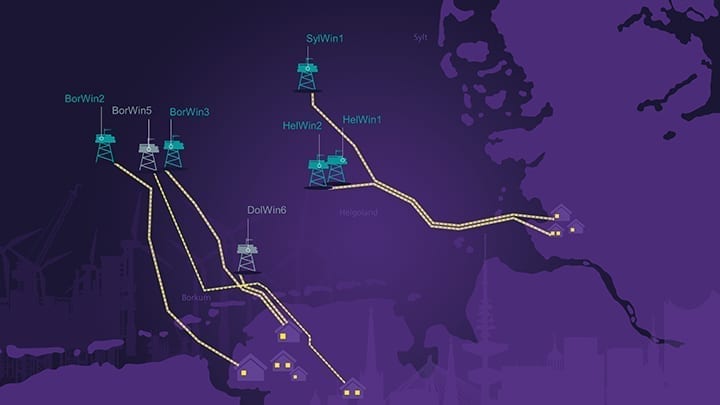
For four days the hired hackers looked for vulnerabilities in the multilayered C&P system from Siemens Energy and attempted to bypass the security mechanisms. In this case, it’s the control system for connecting the two converter stations in the new offshore grid connection system DolWin6 in the German North Sea (Figure 1). The company is supplying all the technology for efficient DC transmission for DolWin6’s grid connection. The European electricity transmission system operator (TSO) TenneT awarded the contract to Siemens Energy in July 2017. Siemens Energy connects the onshore switchgear to the offshore platform via an HVDC PLUS link—a special, extremely efficient and powerful type of grid connection. The link is designed for a DC voltage of +/- 320 kV.
 |
|
1. Siemens Energy is supplying the technology for a total of seven grid connections off the German North Sea coast, including the connection of the DolWin6 wind farm. The order placed by TenneT includes an HVDC PLUS link between the offshore converter station and the onshore substation in Emden, Germany. Courtesy: Siemens Energy |
“Cybersecurity is of primary importance to complex power transmission projects like the grid connection of a wind farm,” explained Matthias Otto, cybersecurity expert for SCADA and communication systems for HVDC transmission systems at Siemens Energy. “You can’t just pull cybersecurity out of a hat. Every company has to have a unified cybersecurity strategy, standards, and consistent implementation. Only then can our customers and we meet the complex security requirements of critical infrastructures and guarantee a reliable power supply. At Siemens Energy, the protection of products, systems, IT infrastructure, and data starts with the selection of suppliers and continues through product design and engineering, finally culminating in the servicing of a complete system.”
Comprehensive Cyber Strategy
Of course, this hasn’t always been the case. For a long time, many companies had individual procedures for dealing with cyberattacks that were only partially effective and weren’t coordinated. It wasn’t until there were massive attacks by malware programs—most notably the Stuxnet worm that was unleashed on SCADA programs about 10 years ago—that a fundamentally new mindset emerged.
For Siemens, as well, this was the starting point for developing a consistent and comprehensive cyber strategy. Today, cyber protection permeates the entire company and its subsidiaries in multiple layers that are both internal and external, and involve all the stakeholders. It includes mandatory processes for the security of products, systems, and their operation, as well as a specially trained expert team and trusted partners.
In February 2018, Siemens and eight partners from industry initiated the first joint Charter of Trust for increasing cybersecurity. In 2019, Siemens began requiring that all its suppliers comply with minimum mandatory cybersecurity requirements. For example, both the suppliers and Siemens have to incorporate special standards, processes, methods, and tests in their products and services. This approach is intended to prevent software vulnerabilities and infiltration by malicious code, and to better protect the digital supply chain from hacker attacks, both at the supplier end and in Siemens solutions. The main focus is on suppliers of security-critical components, including software, processors, and electronic components for specific control units.
Cyberattacks and Their Consequences
“We all have to stay alert and remember that we’re under constant siege,” said Otto. “In the worst case, a network operator—and therefore all of us as well—would be left in the dark after a blackout. That’s why the resilience of our power transmission systems is of such prime importance.”
Not only are the digital attacks against power plants more and more frequent, they’re also becoming increasingly sophisticated. Their focus has also shifted from information technology (IT) to operation technologies (OT), penetrating as far as the functioning of machines. Instead of spying on data, attackers attempt to interrupt a service or damage critical infrastructures.
The consequences range from the loss of intellectual property and interrupted operations to a complete plant shutdown, with the associated severe economic losses and reputation damage. Perpetrators of attacks aren’t just individuals; now they include organized crime groups, terrorists, and industrial spies, or they’re supported by governments. The one thing that they all have in common is that they seek out and exploit vulnerabilities in the system. So, how can systems be made more resilient?
“Cybersecurity, IT, and OT experts have to work together before and during a crisis, quickly recognize attacks, and respond,” said Otto. “What’s clear is that regardless of the motive, origin, or type of cyberattack, our job is to prepare our customers and ourselves for every scenario.”
Many Layers of Protection
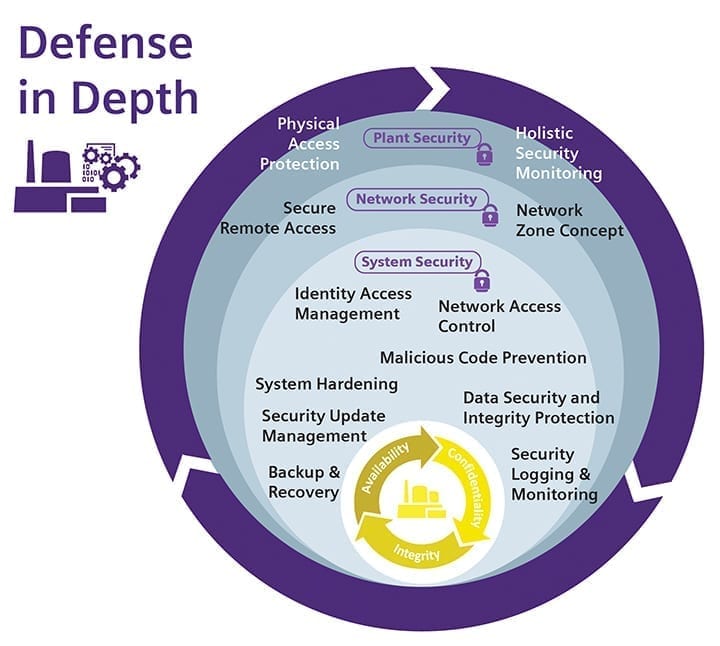
To maintain a high level of security from the very start of every project and beyond, fundamental measures have to be taken (see sidebar). Otto compared these security layers to the layers of an onion, where the innermost core—the plants, networks, and systems—is protected by many outer layers.
Cyber Best PracticesSome of the most important rules and tips that users can apply are listed below. Identify Cyber Vulnerabilities. The following items can help reduce vulnerabilities:
Protect Your Systems. It’s important to comply with all international cybersecurity standards. Going further, a core element of a comprehensive protection program involves examining and improving technological security aspects. This nested security architecture (Defense in Depth) comprises many complementary measures on different layers (Figure 2).
The outer physical plant security layer (for example, access control and surveillance cameras), the network security layer (perimeter security, including a network zone concept—central firewall—and secure remote access), and the inner system security layer. The latter includes:
Respond to Cyber Incidents. In the event of a cyber incident, immediately contact your customer service hotline. Customer service at Siemens Energy is supported by the central ProductCERT expert team, whose experts analyze the cyber incident, assess the potential repercussions, and support damage limitation and repair measures. Following the attack, restore the systems, using backups if necessary. Take Advantage of Consulting and Ongoing Education Opportunities. Provide training on international cybersecurity standards for yourself and your staff. For the best results, get internal and external security experts involved in the program. |
Secure Power Transmission for DolWin6. What exactly does this mean for a power transmission project like DolWin6? “Our work on a cybersecurity project starts as early as the bid phase,” explained Matthias Claus, technical project manager for DolWin6 at Siemens Energy.
It might work something like this: First of all, the riskDNA software that Siemens developed specifically for this purpose automatically searches the customer bid. Bid processors evaluate the results and inform the responsible IT security manager of the customer’s specific requirements.
“Cybersecurity is already part of the bid,” said Claus. “Once the contract is signed, a thorough consultation is held with the customer, an analysis of threats and risks is performed, and a specification is prepared that state how we envision the cybersecurity concept and how we’ll coordinate this strategy with the customer.”
46 Pages of IT Security. The core feature of the cybersecurity concept for DolWin6, as for every project, is the Defense-in-Depth approach. This approach defines various hierarchical levels of devices and procedures, and establishes multiple barriers. Critical data and systems are protected independently by means of physical (access restrictions), technical (security services), and administrative (account/role definitions) controls. This creates multilevel protection comprised of different layers. If an attacker penetrates one level, the attack should be blocked by the next level.
For DolWin6 alone, Siemens Energy’s IT security specification is 46 pages long. It also defines, for example, the physical protection of plants: “All rooms containing critical assets (like the platform control room) are equipped with a door security system that prevents unauthorized persons from entering.”
This is followed by the secure system architecture that includes, for example, the “minimal need to know” principle, meaning that users and system components have only the minimum authorizations and access rights that they need to perform a specific function. This is the company’s way of implementing complementary security technologies on multiple system levels in order to minimize security threats throughout the entire network. The results of the specification are later incorporated into the final documentation for IT security, which comprises several hundred pages.
Comprehensive Test of Original Equipment. Are standards being complied with? According to Otto and Claus, this is ensured by comprehensive procedural measures, and internal and external tests, like the pen test described above. To perform these tests, Siemens Energy assembles all the control technology equipment before delivering it to the company’s own premises.
The external testers employed for DolWin6 were from the independent Berlin-based audit specialists GAI NetConsult. The company conducted the pen test for DolWin6 in Erlangen in May 2020. The professional hackers determined that the C&P system for the wind farm link was ready to begin operation. “For a complex energy project like DolWin6, a successful pen test is an extremely important cybersecurity milestone,” Claus said.
The project is currently ready to complete the FPT. “When the FPT is performed at the end of 2020, the focus will once again be on cybersecurity,” explained Otto. “We perform these tests in-house. At the beginning of 2021, following a successful test, we’ll transport the entire control plant comprising two sections to the two locations in Emden, Germany, and Cadiz, Spain, and will reassemble them there.” The land-based station with the HVDC link will be built in Emden, and the offshore platform that will hold the second converter will be produced by the Spanish shipyard in Andalusian Cadiz. Then there will be nothing left to prevent the secure connection of the new wind farm.
Where Is This Digital Journey Headed?
As the World Energy Council states in one of its recent publications, “The digitalization of the energy industry will continue.” The industry is relying more and more on interconnectivity, which is why cybersecurity needs to remain a central concern.
The same is true of dynamic resilience, which is the capacity to continuously adapt—sort of like a muscle that needs constant exercise. “In the past, digital connectivity via a cloud or the Internet of Things in the energy sector was still the exception,” said Otto, “but now we’re seeing a trend toward more comprehensive data analysis, in order to enable predictive maintenance, for example. But the way things are headed, all stakeholders will have to be prepared for any scenario. Cyber threats are lurking everywhere. Hackers never sleep. They’re becoming more agile, faster, and more ingenious.” ■
—Nina Terp is a technical journalist based in Germany.