A discussion draft of a preliminary cybersecurity framework posted by the National Institute of Standards and Technology (NIST) last week outlines several functions to protect industrial control systems, but it acknowledges that the power sector already engages in several cybersecurity practices and recommends that utilities opting to use the framework should leverage these rather than duplicate efforts.
NIST was directed by President Obama this February to collaborate with industry to develop a voluntary risk-based cybersecurity framework. As part of efforts to develop the preliminary framework, the measurement standards laboratory on Aug. 28 issued “A Discussion Draft of the Preliminary Cybersecurity Framework” to encourage comments ahead of the fourth Cybersecurity Framework workshop that will be held in Dallas, Texas, on Sept. 11-13.
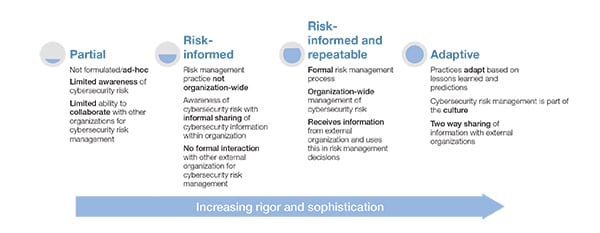
The document’s executive summary describes the framework as a uniform guide for developing “robust cybersecurity programs for organizations. This includes industry-driven standards, best practices and implementation measures to manage cybersecurity risks to information technology and operational technology.” The framework also provides a “common structure” for managing cybersecurity risk. Cybersecurity activities are essentially divided into five key functions that owners and operators of the nation’s critical infrastructure are urged to implement: to identify, protect, detect, respond, and recover.
Of special significance for the nation’s power sector, on Aug. 30, NIST also released a draft illustrative framework example of how the framework would work for owners or operators of industrial control systems (ICS).
That document recognizes that ICSs behave differently than a traditional IT-based system and therefore require “unique considerations for security. For example, many of these critical ICSs have legacy equipment that cannot be patched or upgraded for years or decades. Some sectors have existing programs or regulations surrounding the protection of these vital systems.” It also notes that “the electricity subsector has created several guidelines, standards, and programs based on cybersecurity practices and controls. Any utility that opts to use the Framework should leverage these existing materials, rather than create new-and perhaps duplicative-efforts.”
If an electric utility complies with North American Electric Reliability Corporation (NERC) Critical Infrastructure Protection (CIP) Version 3 standards, has identified Critical Cyber Assets (CCAs), and has performed a Department of Energy Subsector Cybersecurity Capability Maturity Model (ES-C2M2) self-evaluation, the framework will provide the utility with a number of categories and subcategories for process evaluation and refinement. In the “protect” function, for example, the category “awareness and training” calls on operators to “provide awareness and training that ensures that general users understand roles and responsibilities and act accordingly.”
Public comments on the discussion draft can be sent to NIST via e-mail to cyberframework@nist.gov.
Sources: POWER, NIST
—Sonal Patel, Associate Editor (@POWERmagazine, @sonalcpatel)