Identifying CIP Version 5 Assets in Generation
The latest version of Critical Infrastructure Protection standards applies to different facilities and assets than previous versions, so the first, critical step in compliance is to determine which facilities and assets are subject to the new standards.
Generators of electric power face a big effort to comply with the upcoming North American Electric Reliability Corp. Critical Infrastructure Protection (NERC CIP) Version 5 (V5) cybersecurity standards. Whether or not your facility has had to comply with previous NERC CIP standards, a plant’s cost of compliance will depend directly on the number of “cyber assets” that are in scope. This article is intended to give a basic overview of how generators can identify the cyber assets in scope for CIP V5.
Is It a Bulk Electric System Facility?
The first step is to determine if a facility is in scope for CIP V5 at all. According to the new Bulk Electric System (BES) definition, if a generating facility is connected to the grid at 100 kV or higher, it is a BES facility (with a few exceptions), and it is in scope for CIP V5.
The next step is determining whether the plant is “Medium” or “Low” impact under V5. Generation facilities are not considered “High” impact; this status is reserved for BES control centers that meet specific criteria. For the criteria for classifying facilities in CIP V5, see Attachment 1 of CIP-002 version 5 (written as CIP-002-5) online (http://bit.ly/ShrWQJ).
There are only two criteria in NERC CIP-002-5 that classify generation as Medium impact. In Attachment 1 of CIP-002-5, a generating station is Medium if “a group of generating units at a single plant location” can generate 1,500 MW. Additionally, a generating station is Medium if the Planning Coordinator or Transmission Planner informs you that your plant, or specific unit(s) in the plant, are required to operate for reliability purposes (“reliability must run”). If your plant does not meet one of these two criteria, it is defined as Low impact.
If your generating station is considered Low impact, there is no requirement to identify individual Low-impact cyber assets, and this will remain true for the new Low-impact requirements being developed by NERC in response to the Federal Energy Regulatory Commission’s directive in Order 791. As a Low-impact asset, the rest of this article won’t directly apply to your generating station.
However, if your whole plant or individual unit(s) are Medium impact, the first step is to inventory your cyber assets, defined as “programmable electronic devices.” This includes servers, workstations, distributed control system (DCS) controllers, programmable logic controllers (PLC), and other devices involved in the operation of the generating station.
However, not all cyber assets will be in scope for CIP V5, even at a Medium-impact facility. Those that are in scope are called “BES Cyber Assets.” These are grouped into “BES Cyber Systems,” to which the CIP V5 requirements apply.
There are two basic approaches to identifying BES Cyber Systems: “bottom-up” and “top-down.” These aren’t mutually exclusive; in fact, at least two of the NERC regions recommended that NERC entities use both approaches, because it is possible that some BES Cyber Systems will be missed if only one is used.
Bottoms Up
In the bottom-up approach, generators would evaluate each cyber asset in operation in a plant (for example, servers, operator stations, routers, switches, PLCs, remote terminal units, and so on) and determine if it meets the definition of BES cyber asset, according to the NERC Glossary: “A Cyber Asset that if rendered unavailable, degraded, or misused would, within 15 minutes of its required operation, misoperation, or non-operation, adversely impact one or more Facilities, systems, or equipment, which, if destroyed, degraded, or otherwise rendered unavailable when needed, would affect the reliable operation of the Bulk Electric System.”
This isn’t an easy definition to digest, but it essentially says that the cyber asset must have an impact on the Bulk Electric System within 15 minutes if it is misused, degraded, lost, or compromised. “Impact on the BES” typically means impact on the generating station that hinders or prevents it from fulfilling its purpose (that is, generating power when required).
For example, the DCS will very likely have an impact in under 15 minutes, so the component cyber assets will be BES cyber assets. In another example, characteristics of a particular coal-handling system might allow it to be inoperable for hours or days before the plant has to shut down, so its coal-handling cyber components won’t be BES cyber assets.
The best starting point for inventorying cyber assets is the control system drawings, network drawings, and IP address lists. Generator control becomes the starting point, and other systems are next (Table 1). In a typical control system, about half the devices are IT-type technology (computers or networking) and the remainder are control system devices (including DCS controllers, serial converters, and PLCs). All these cyber assets require inspection and inventory, plus a determination on whether or not each cyber asset meets the BES cyber asset definition (it affects the BES within 15 minutes).
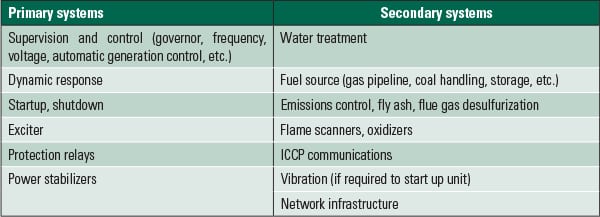 |
| Table 1. Typical generation cyber assets and systems. Source: Honeywell |
Once BES cyber assets have been identified, they need to be grouped into BES Cyber Systems. This is an exercise left to the discretion of the generator. Generators can reduce compliance paperwork by grouping many BES Cyber Assets into a single large BES Cyber System. However, if a generator defines the BES Cyber Systems too expansively, the generator may end up including BES cyber assets that don’t meet the definition, unnecessarily increasing the compliance effort. As a general rule, most consultants familiar with CIP will create BES Cyber Systems by grouping cyber assets that work together to fulfill a function (such as control, continuous emissions monitoring system, or protection).
Take It from the Top
The top-down approach starts with the BES Reliability Operating Services (BROS), which are discussed in the “Guidelines and Technical Basis” of CIP-002-5. The BROS are reliability services that BES facilities can provide to the grid. Table 2 identifies those BROS that would typically apply to generation owners (GO) and generation operators (GOP). (If the BROS don’t make immediate sense, refer to Table 1, which lists potential BES Cyber Systems in a power plant.)
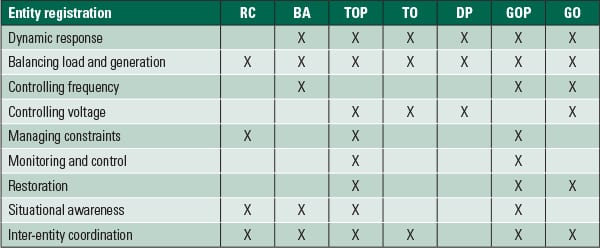 |
| Table 2. BES Reliability Operating Services. Source: CIP-002-5.1 Guidelines and Technical Basis |
The systems that fulfill one or more BROS should all be considered “potential BES Cyber Systems.” But because a BES Cyber System is composed of BES Cyber Assets, you need to go back to the BES Cyber Asset definition and make sure it still applies. For instance, if a “potential BES Cyber System” doesn’t have a 15-minute impact on the Bulk Electric System, then it won’t be a BES Cyber System, even though it does fulfill a BROS function.
Before a “potential BES Cyber System” becomes an actual one, there is one more step to take. The generator needs to go back to the definition of BES cyber asset (cited above) and make sure each “potential BES Cyber System” meets the definition. In particular, some “potential BES Cyber Systems” may not pass, as they don’t have a 15-minute impact on the BES.
To summarize the top-down approach: Identify the BES Reliability Operating Services that are performed by the generating station and then identify the BES Cyber Systems that execute or enable one or more BROS. The BES Cyber System classification as Medium or Low depends on the impact level of the plant.
Large Plants
If a generating facility meets Criterion 2.1 of Attachment 1, there is a further provision in that criterion that states: “the only BES Cyber Systems that meet this criterion are those shared BES Cyber Systems that could, within 15 minutes, adversely impact the reliable operation of any combination of units that in aggregate equal or exceed 1500 MW in a single Interconnection.”
This statement indicates that the generating facility could be Medium impact, but it may have few or no Medium-impact BES Cyber Systems, because a BES Cyber System has to have the capability of affecting the entire generating station. A good example of this condition is a DCS that controls only 800 MW of generation at a 1,600-MW facility and has no capability to affect the full 1,600 MW at the site. In this example, the plant would be Medium impact, but the DCS is a Low-impact BES Cyber System.
Generators looking to reduce their CIP compliance burden by taking advantage of this provision need to keep in mind that simply stating that the BES Cyber Systems cannot affect 1,500 MW will not be sufficient. They will need to prove this position by showing the work related to the identification of BES Cyber Systems through the bottom-up and top-down approaches. The generator must also document why each BES Cyber System doesn’t affect 1,500 MW and show that it isn’t networked with other BES Cyber Systems that do affect 1,500 MW.
Complex Determinations
The asset identification process in NERC CIP Version 5 is much more complicated than it was in CIP Versions 1 through 3. If a generating station will be classified as Low impact in V5, the process won’t be excessively difficult. But owners of Medium-impact generating stations will require a deep understanding of how to identify cyber assets in scope. The cost and effort required to achieve NERC CIP V5 compliance will depend heavily on this understanding. ■
— Tom Alrich ([email protected]) is energy sector security lead for Honeywell International and focuses on the electric power industry and compliance with NERC regulations for cyber and physical security. Donovan Tindill, CISSP, senior security & compliance consultant, Honeywell Industrial IT Solutions, specializes in cybersecurity for industrial automation and control systems for a wide variety of industries and has been involved with NERC CIP compliance since 2005.